The “interface-less” mode is when static routes are used and the interface isn’t configured with an IPv4 address because it isn’t mandatory to establish a phase 2 tunnel. In a highly-scalable environment, you’ll find yourself repeatedly adding static routes after adding another set of Proxy ID entries (IPSEC Phase 2) and mistakes are bound to happen. This is where a dynamic routing protocol such as OSPF shines.
This post is only intended for those who do have site-to-site IPSEC configured with static routing.
Assumptions
- Have an IPSEC tunnel up and running
- Familiarity with security policies
Overview
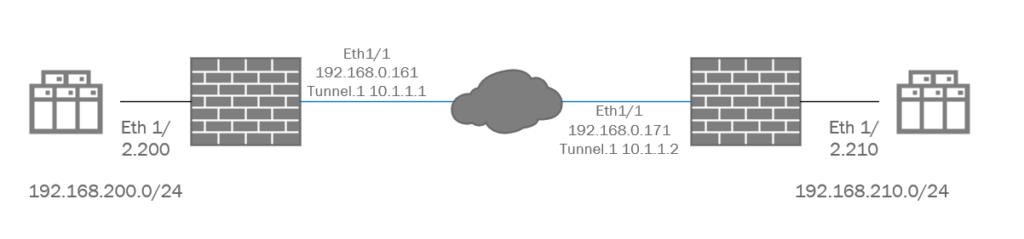
This IPSEC topology is as basic as it can get. With two peers and two local networks participating in the IPSEC VPN.
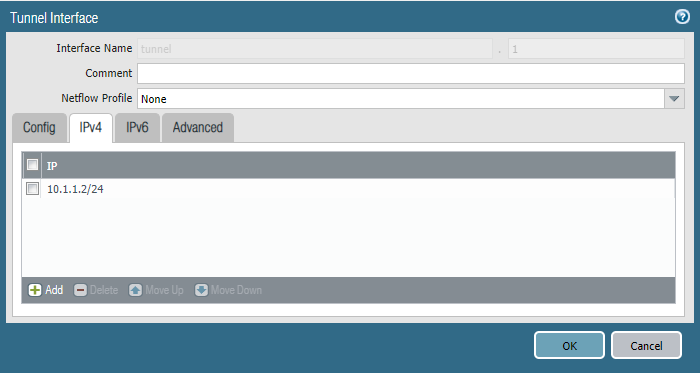
Tunnel Interface
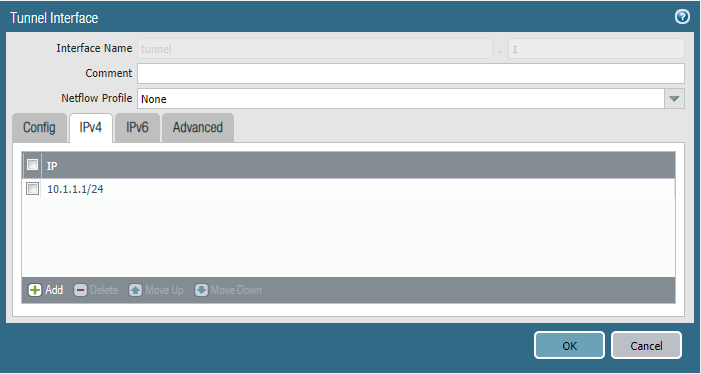
We’ll start off with adding an IPv4 address to our tunnel interfaces at site 1 and site 2. Make sure both of them are in the same subnet and the prefix does matter as well.
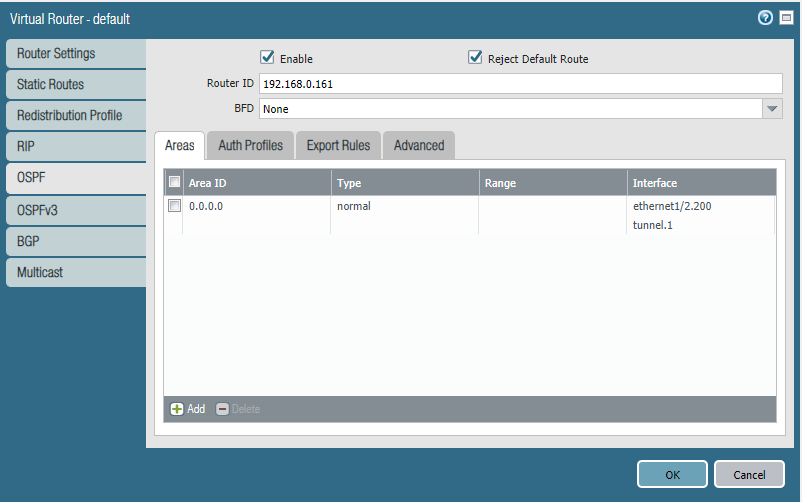
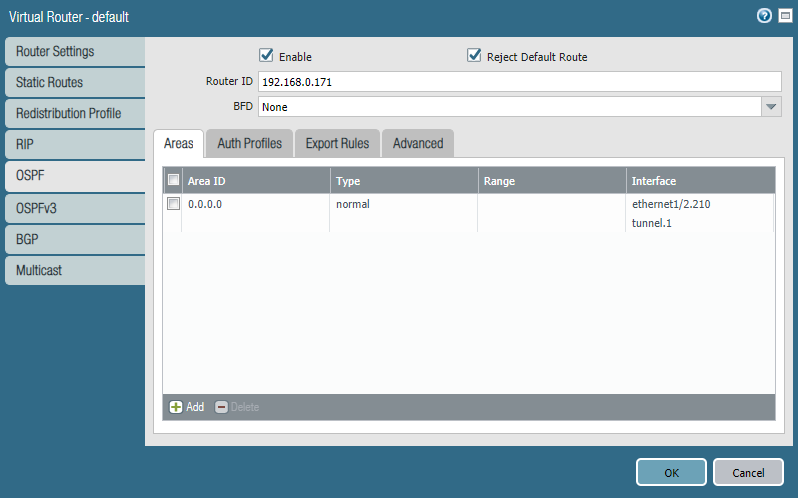
Virtual Routers
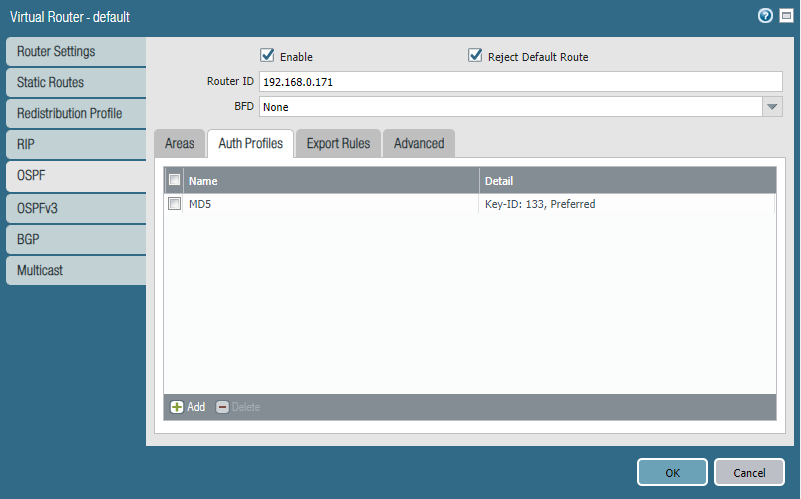
The Router ID here is the value that will present itself to OSPF neighbors. To keep it simple I’ve used the public IP-address of this firewall, although whatever value you’ve decided – it doesn’t matter. “Reject Default Route” basically means that OSPF won’t advertise the firewall’s default route (0.0.0.0/0) because usually firewalls are already configured with a default route.
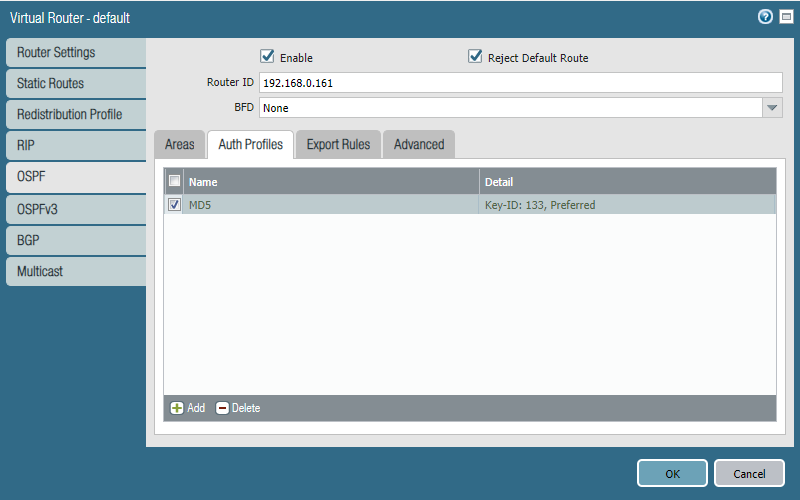
(Optional) We can configure an authentication profile as a security measure to avoid advertising routes to unintended peers.
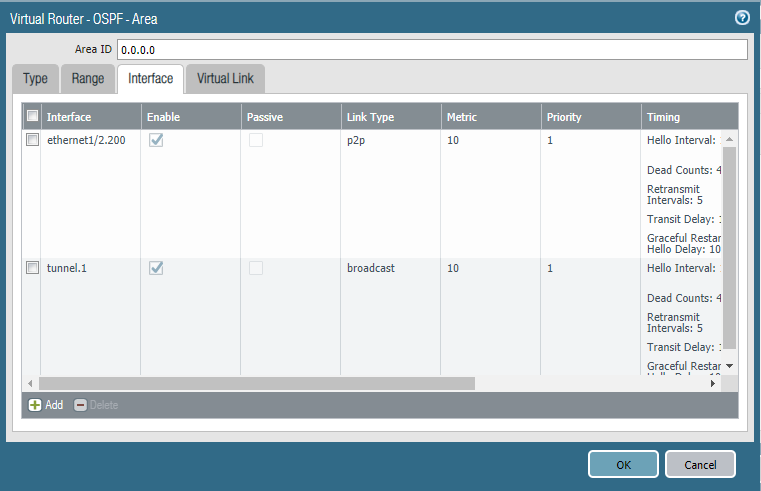
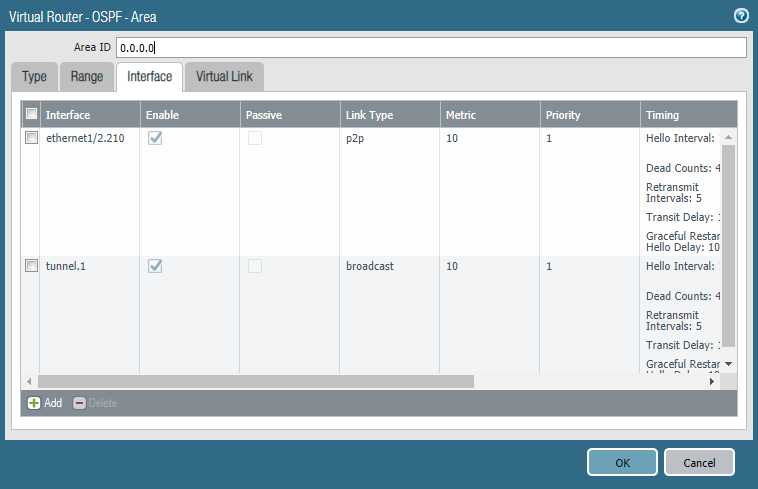
Next, we’ll add an area 0.0.0.0 and add our tunnel interface and the interfaces of our local network(s). The tunnel interface should be configured as “broadcast” while the local network’s interface should be “P2P”. Do not forget to include the Auth Profile if you intend to use it.
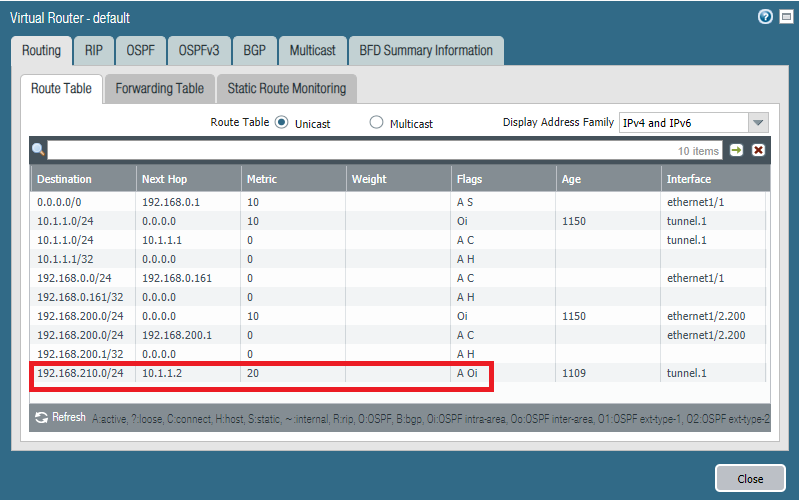
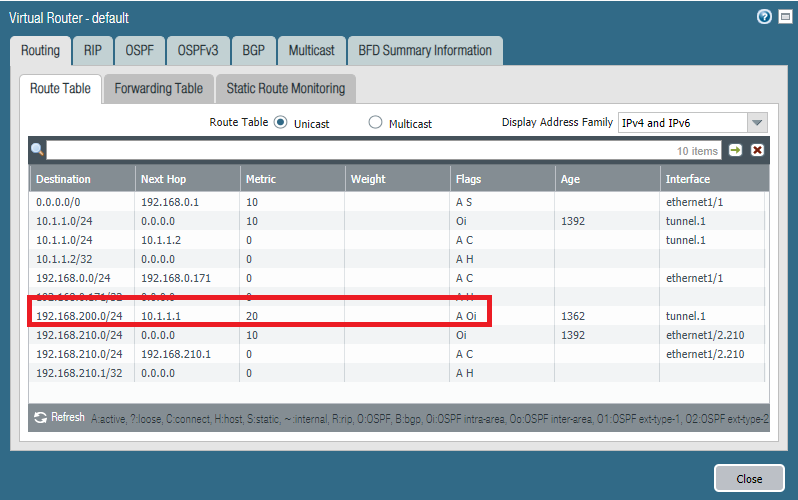
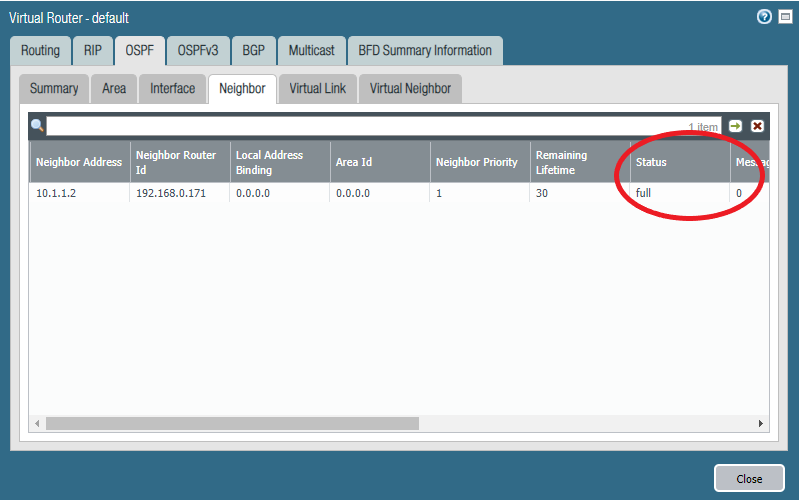
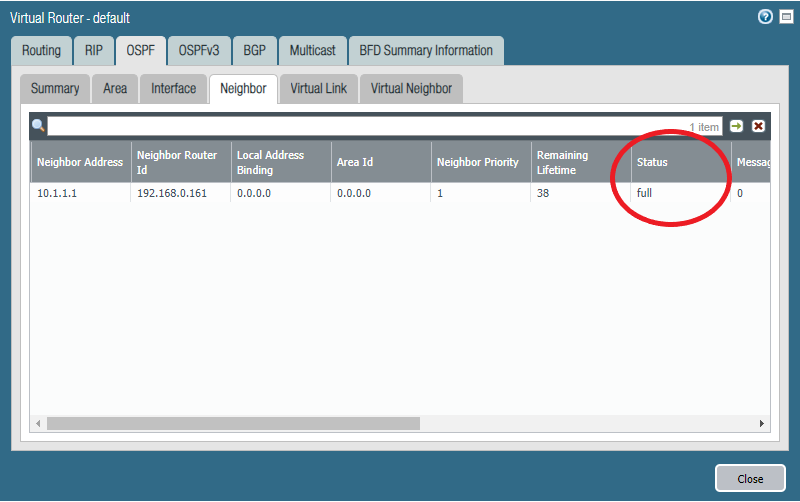
Verifying neighbors and routes
We should see that the status with the neighbor is “full” meaning that neighbor adjacency is fully formed.
We should see the routes being advertised by OSPF, through the Tunnel.1 interface with its IP-address as next hop. The “O” flag stands for OSPF and “i” for intra-area since there’s only a single area available.