The NSX-T builtin firewall is quite refined, but it lacks so much of what Palo Alto Networks and their cloud services have to offer. Traffic can be redirected to a VM-series firewall for inspection with the use of security profiles and it provides more granular control over your policies with App-ID. The NSX-T firewall can be ignored for the most part because security policies are configured in Panorama.
Prerequisites
- NSX-T Manager/Edges up and running
- Palo Alto Networks Panorama
- A support account (support.paloaltonetworks.com)
- VM series auth codes to license the firewall (VM100 series as a minimum)
- HTTP/HTTPS web-server to host the NSX-T signed images
Deployment options

A service insertion is basically attaching the VM series firewall either to the T0 or T1 gateway. We cannot add more than one service insertion per gateway, but we do have the option to add firewalls in high-availability mode per gateway.
We decided to attach it to our T0 gateway because we’re planning to add an east-west service insertion to our T1 gateway for another post. ‘North-South’ traffic indicates either internet traffic because it’s external or to another datacenter with a different T0 gateway. Where as ‘East-west’ is basically traffic moving between VM’s.
Topology overview
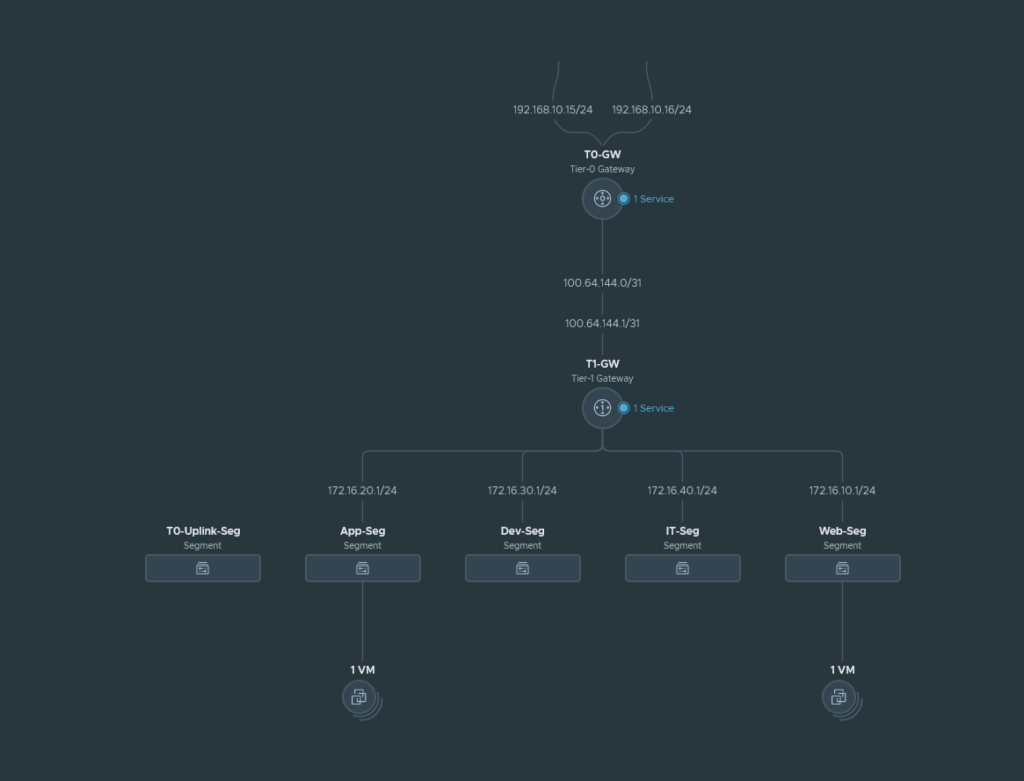
We have 4 segments (App, Web, Dev and IT) behind a T1 gateway and this T1 gateway connects to our T0 gateway. The T0 gateway is behind the upstream router and the local network for it is 192.168.10.0/24. The management address of the VM-Series we are about to deploy will also be in the 192.168.10.0/24 range.
The T0-Uplink-Seg is used for the service interfaces on our T0 gateway that connects to our upstream router.
The North-South Service Insertion will be attached to the T0-GW because we are trying to inspect traffic leaving the T1 gateway such as internet traffic. The VM-Series firewall will sit in between the T0/T1 GW and the T0 is considered as ‘North’ and T1 as ‘South’. East-West traffic e.g. intra-VM from our segments will not be inspected by this type of service insertion.
Preparing the T0 Gateway
The T0 gateway has to be in Active/Standby mode because Active/Active HA is not supported as an attachment point which we will get to when deploying a service insertion later on.
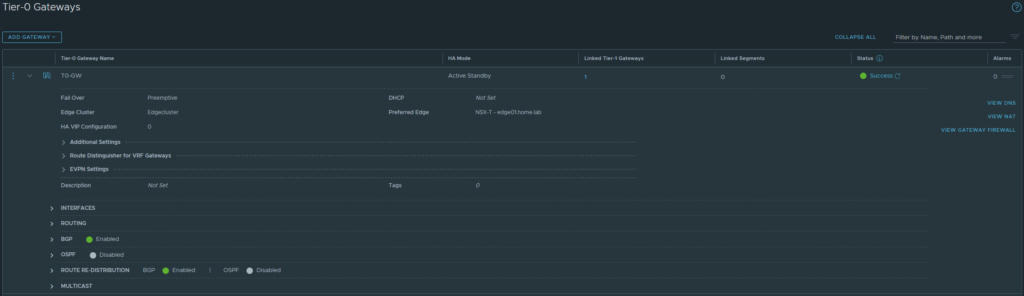
Installing the plugin and linking Panorama with the NSX-T Manager
Install the NSX plugin which can be found under Panorama > Plugins and make sure to get the latest version. We have to add a service manager to link Panorama with NSX-T. Panorama > VMware > NSX-T > Service Managers.
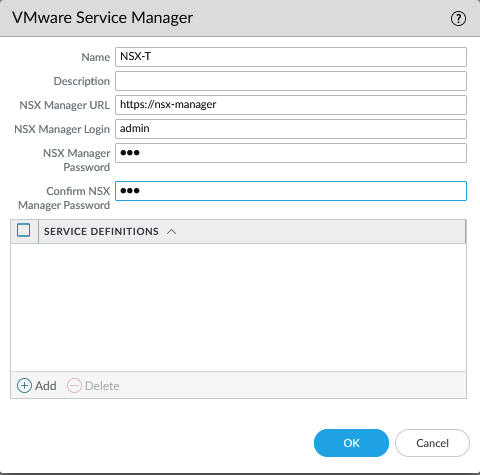
Commit to Panorama. The status should show as ‘Registered’ if successful.
Creating the Device Groups, Template and Template Stacks
Simply create the following.
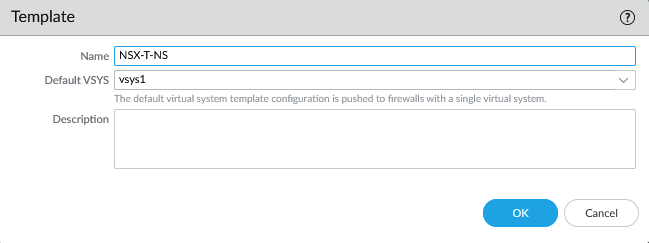
- Template: NSX-T-NS
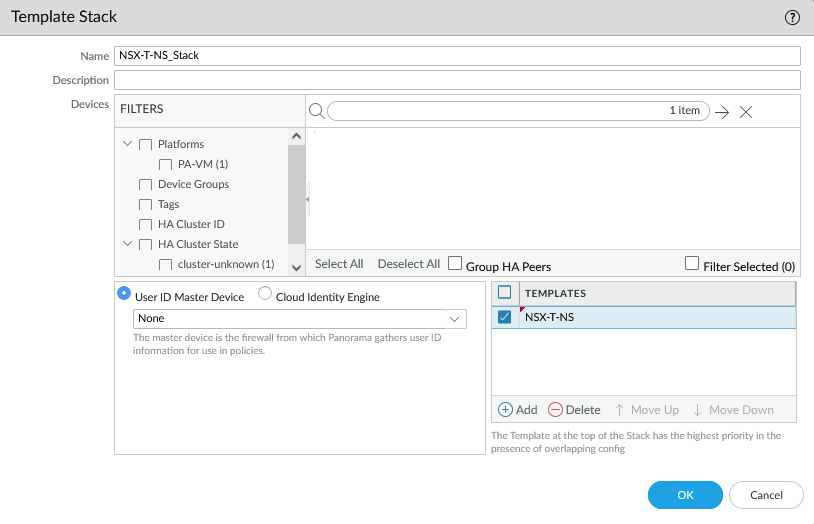
- Template Stack: NSX-T-NS_Stack
- Device Group: NSX-T-NS
The template.
The template stack.
Add the Device Group.
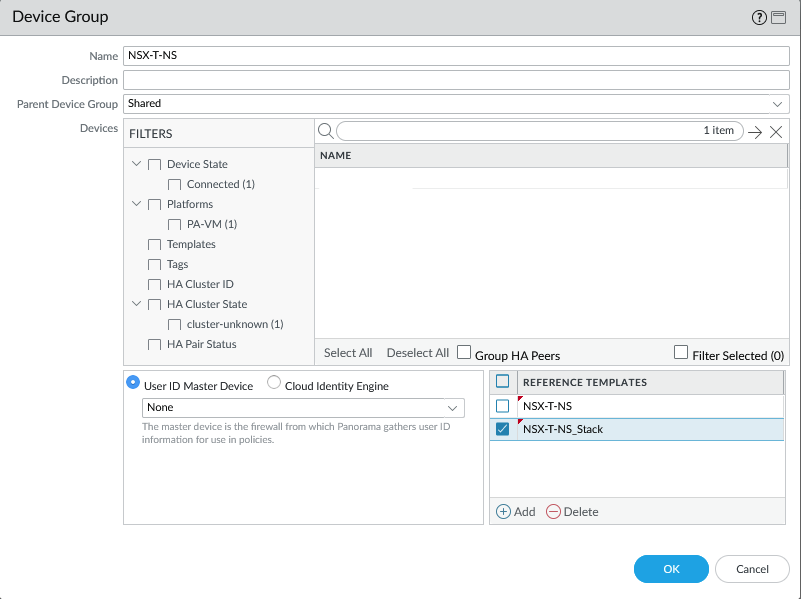
Make sure to add the template and template stack as a reference in the Device Group so that security zones show up in your policies.
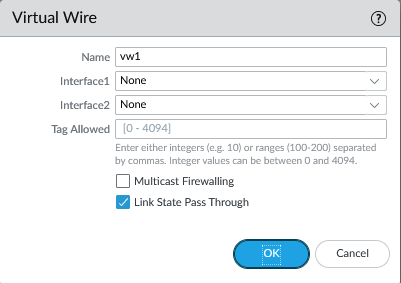
Next, select the ‘NSX-T-NS’ template (NOT the stack) and under Network > Virtual Wires add a vwire object.
Under Network > Interfaces
- Configure ethernet1/1 with ‘south‘ as the security zone and as a virtual wire interface type.
- Configure ethernet1/2 with ‘north‘ as the security zone and as a virtual wire interface type
‘North’ is where the traffic will be exiting to and ‘South’ is the side where the VM’s are at.
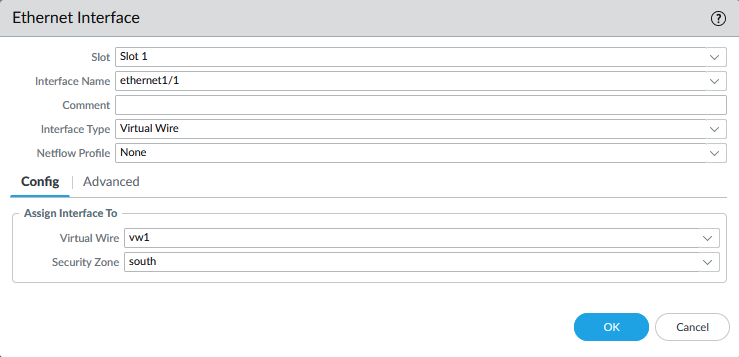
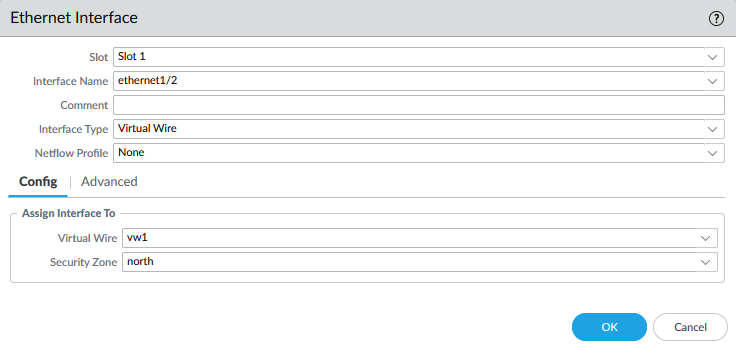
Commit to Panorama.
Configuring service definition
We have to provide a device PIN ID and value starting from certain PANOS versions. On the support page, generate the pair. It’s under Assets > Device Certificates

Copy the PIN ID and the PIN value for later.
Next, we’ll add the service definition. Panorama > VMware > NSX-T > Service Definitions. Make sure the URL hosting the NSX-T images are functional. Select the template, stack and the device group we created earlier. Copy paste the PIN ID and value here as well. Make sure to select the north-south insertion type.
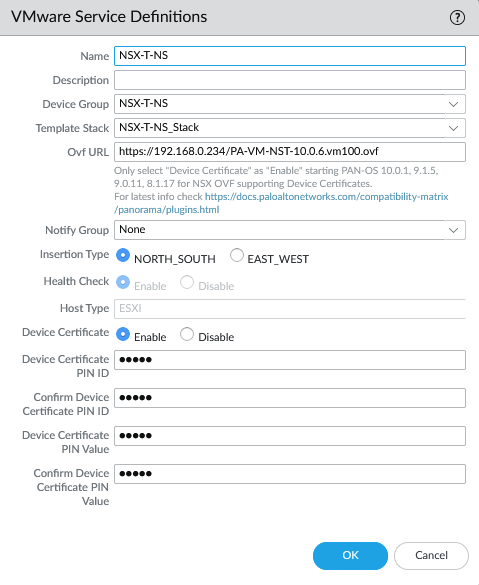
Add your VM-Series auth code on the Device Group level. This step is required or else it will fail to commit the configuration of the plugin.
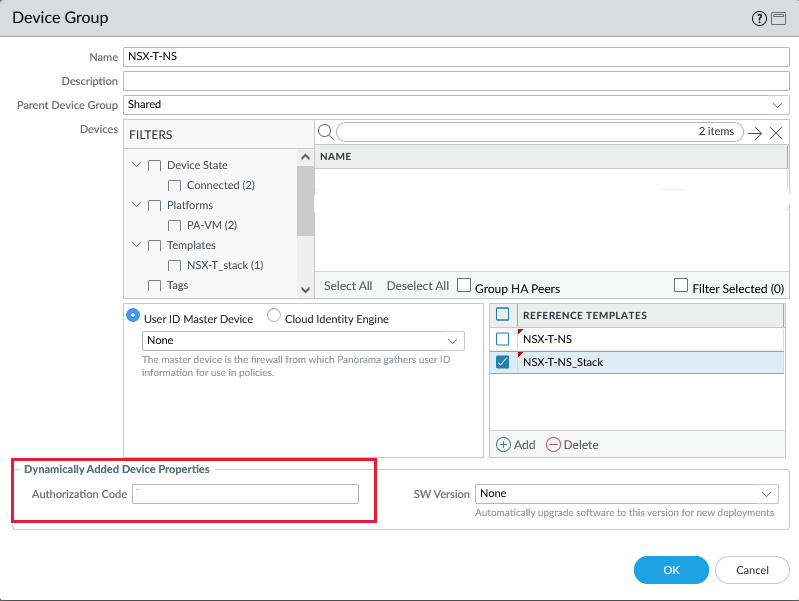
The last step is to add the service definition to the service manager under Panorama > VMware > NSX-T > Service Managers
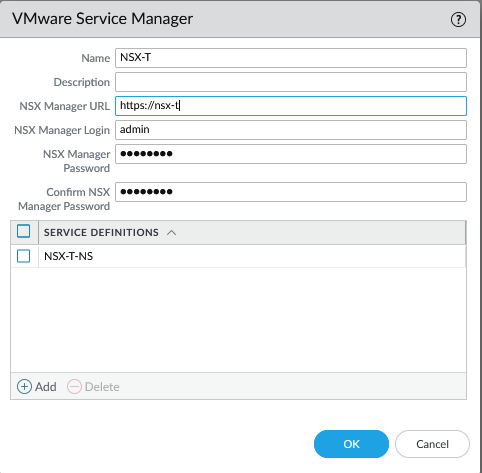
Commit to Panorama.
Deploying the VM-Series firewall
We can deploy the VM-Series firewalls from the NSX-T Manager. Head over to System > Service Deployments. We can see the Partner Service ‘NSX-T-NS’ definition we created earlier in Panorama. Deploying the service requires a few configurations and it’s rather automated at this point. Device certificates/licensing are also automated along with the integration and syncing with Panorama and highly recommended to double-check this.
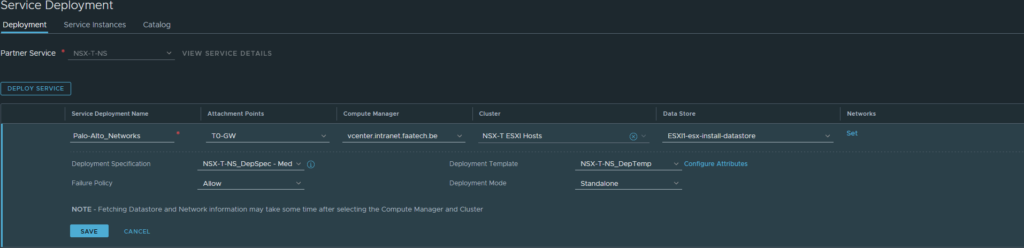
Select the T0 gateway and the cluster/datastores. The deployment mode can be Active/Standby which is basically High-Availability, but we’ve opted for a standalone deployment mode because of limited licenses. Make sure to configure the network, which is just the management interface and it has to be a network that Panorama can get to. Add the necessary routes if needed or Panorama won’t be able to manage it. ‘Failure Policy’ is basically whether traffic should be allowed or not when the VM-Series firewall goes down.
The status should be successful once it’s done deploying the firewall.
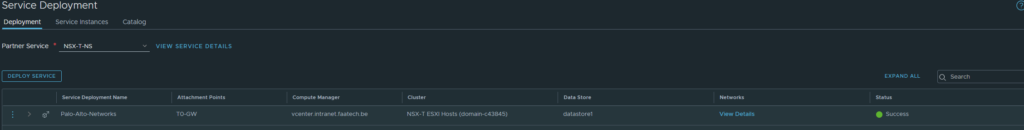
After it’s complete, make sure the config files of Panorama/VM-Series are in sync before going forward. Panorama > Managed Devices > Health

Redirecting traffic to VM-Series Firewall
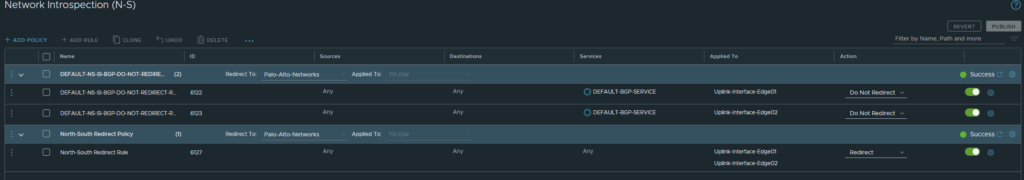
Head over to Security > North South Security > Network Introspection (N-S). There should be a default rule added and do not edit this. The default rule basically does not redirect BGP traffic to the VM-Series firewall and the reason behind it is to prevent from BGP breaking because by default the VM-Series Firewall does not allow any traffic due to no security policies being added.
Make sure the default BGP rule is at the top. Add a new Policy/Rule under the BGP policy and select the Uplink interfaces or your Edge (the service interfaces that connect to the upstream router).
Pushing security policies from Panorama
Make sure to double check that Panorama and VM-Series firewall configs are in sync (Panorama > Managed Devices > Health).
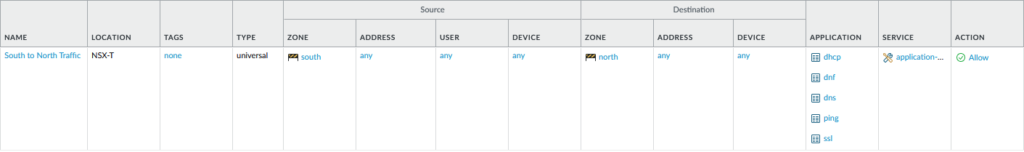
A few applications such as SSH, Ping etc. have been allowed in the following example. Test whether the firewall actually blocks applications that you didn’t specify in the rule.