Duo is one of the so many enterprise-grade identity providers that support SAML (SSO) and RADIUS authentication methods for an extensive list of apps to configure. Duo is free for up to 10 users, but lacks SAML support and a lot more unless you opt for a paid subscription. SAML over RADIUS is highly recommended because of its single-sign-on nature and it’s by far more secure. Another reason is that SAML doesn’t require on-premise agents because it’s a cloud service, which takes the need of fail-over mechanisms out of the equation and SAML is ubiquitous with other applications unlike RADIUS.
This guide will cover the configuration of RADIUS authentication paired with Active Directory.
Pre-requisites
- GlobalProtect Portal + External Gateway configured
- Duo Free Edition Account
- Duo MFA App installed on a mobile device
- Active Directory Domain Controller
- User-ID configured with Active Directory Authentication
Initial configuration over at DUO
Let’s install the Palo Alto SSL VPN Application:
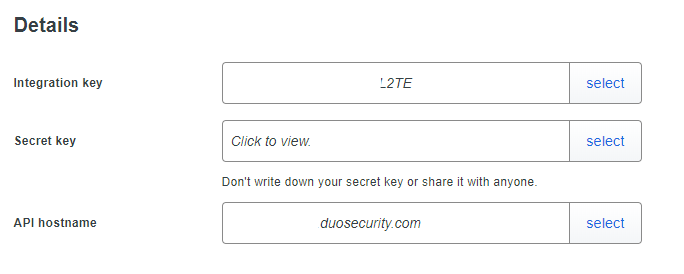
Once we open it, we’ll see the integration key, secret key and the API host (can act as an URL for your organization or whatever). Do not share the secret key with anyone else. We do not need to make any configurations here.
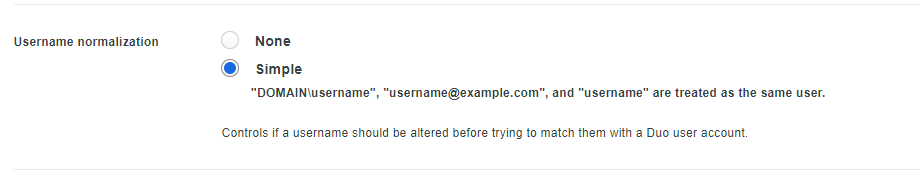
For this application, DUO treats the username formats the same. So we don’t have to add users in a format like “username@example.com”. Meaning we can use the same user for various other applications eg something totally out of this scope; Dropbox, WordPress, Zoom etc… Given that the username actually matches.
So let’s add one:
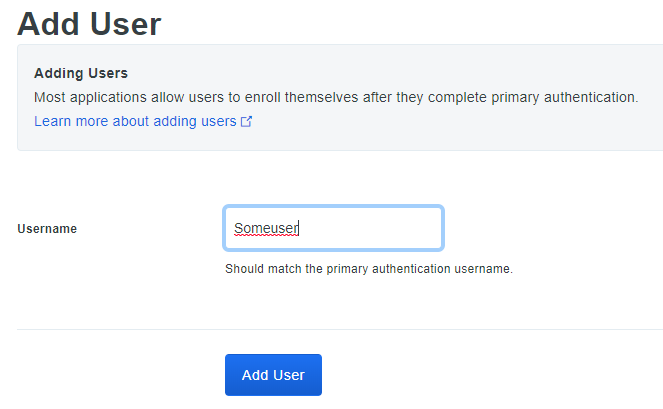
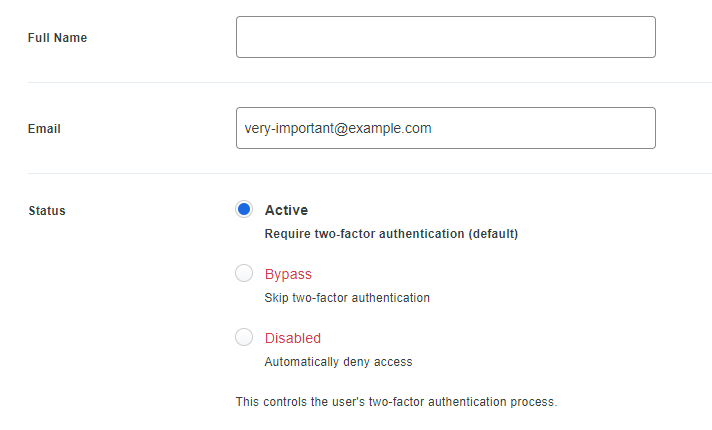
Make sure to enter an e-mail address and check the box “Active” to require MFA.
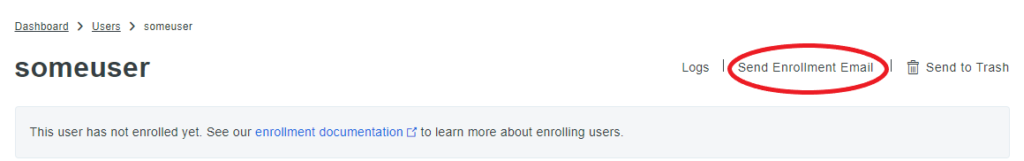
In the top right click “Send Enrollment Email” so users receive a mail with instructions to set up DUO Mobile on their mobile devices.
Installing and configuring DUO Auth Proxy
Get the DUO Auth Proxy from this link. The installation is straight forward but make sure to enable the service. “net start duoauthproxy” in CMD should do the trick.
Remove everything in the authproxy.cfg file located in C:\Program Files\Duo Security Authentication Proxy\conf
Modify the following configuration matching your infrastructure. The “radius_ip_1” should be the default gateway of the Domain Controller you’re installed the Duo Auth Proxy – that’s where the RADIUS request originates from. For example, my default gateway is 192.168.50.2 and the IP address of the Domain Controller with Duo Auth Proxy is 192.168.50.10. Make sure the given domain user is a member of the group “Domain Admins” so it has the privileges of authenticating users.
[ad_client]
host=192.168.50.10
service_account_username=some-AD-Admin-user
service_account_password=some-secure-pass
search_dn=DC=faa,DC=local[radius_server_auto]
ikey=your-integration-key
skey=your-secret-key
api_host=your-API-host
radius_ip_1=192.168.50.2 (default gateway)
radius_secret_1=some-super-secret
client=ad_client
failmode=safe
port=1812
Restart the Duo Auth Proxy Service (CMD).
net stop duoauthproxy && net start duoauthproxy
RADIUS Server Profile and Authentication Profile
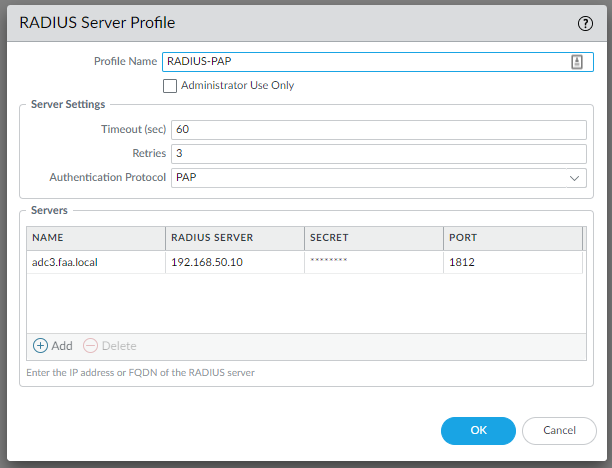
Let’s head over to the firewall and under Device > Server Profiles > RADIUS > Add
Make sure to select PAP, enter the IP address of the Domain Controller with the Duo Auth Proxy installed and the same secret key you defined in the authproxy.cfg file.
We’ll also need an authentication profile. Device > Authentication profiles > Add.
Select the RADIUS Profile and add “All” under the Advanced Tab.
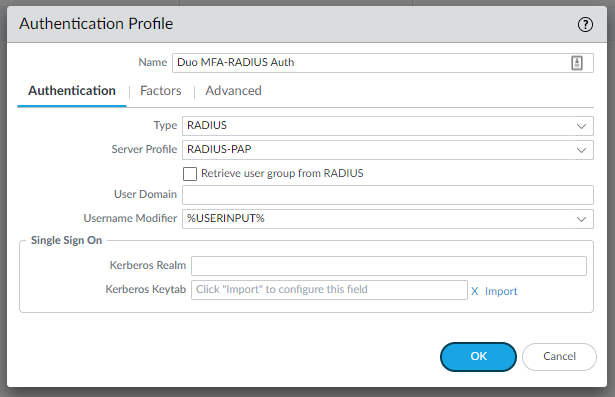
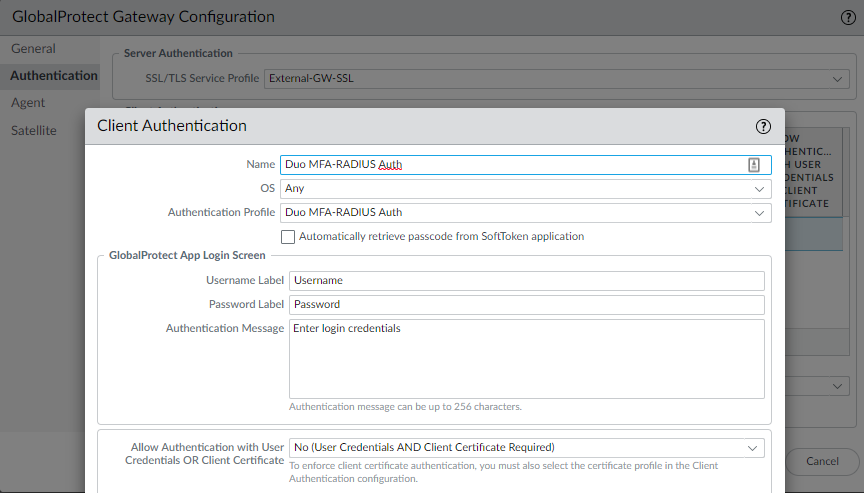
Decide whether you want the RADIUS authentication profile on the GlobalProtect Portal or the gateway, or even both but this makes it annoying for the user because they’ll have to authenticate twice with the Duo Mobile App. It’s better to keep the portal with a plain LDAP Authentication Profile and the Gateway with a RADIUS Authentication Profile.
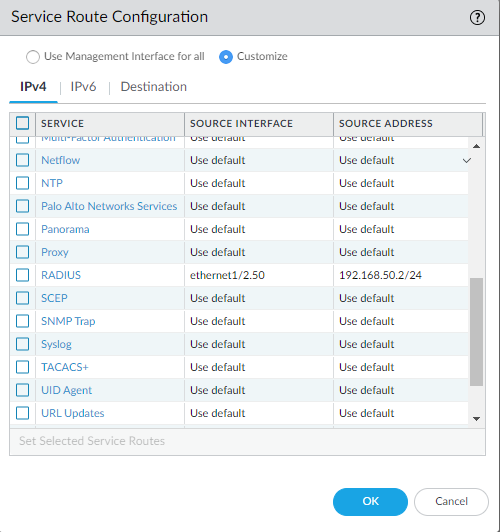
Lastly, we’ll have to configure the service route for RADIUS. Device > Setup > Services
For RADIUS select the interface of the Domain Controller with Duo Auth Proxy installed.