
A virtual wire interface makes it very easy to deploy Palo Alto’s NGFW in an existing network because it doesn’t require you to change any of your IP-addresses or redesigning the entire network – and on top of that we benefit from all the security solutions that Palo Alto provides. It works by binding two ports between a firewall/router and another firewall/router/switch (which be a switch), it creates some sort of a wire or rather a virtual wire within the firewall itself. The routers have no awareness of this happening, thus the terminology “transparent” falls into place.
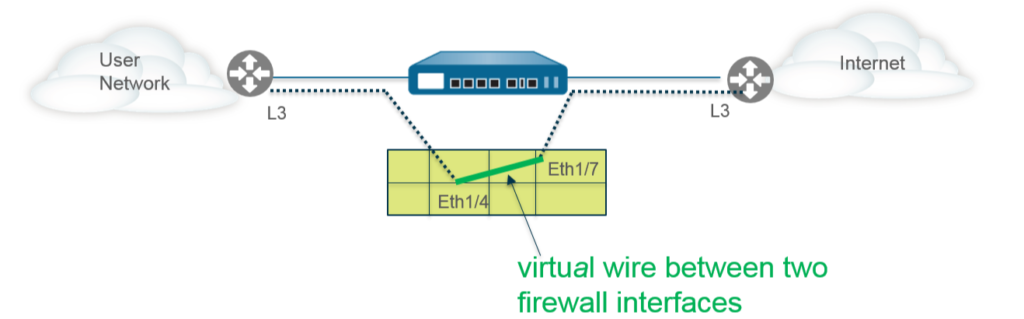
This picture below does an excellent job of illustrating the virtual wire, Eth 1/4 & Eth 1/7 are used on the Palo Alto Firewall which is located in-between the endpoint and the existing router.
Prerequisites
- ESXI host or vCenter for vSwitches/dSwitches
- Knowledge of how to use vSwitches (ESXI) or dSwitches (vCenter)
- A firewall/Router acting as an edge router with internet access
Lab Setup
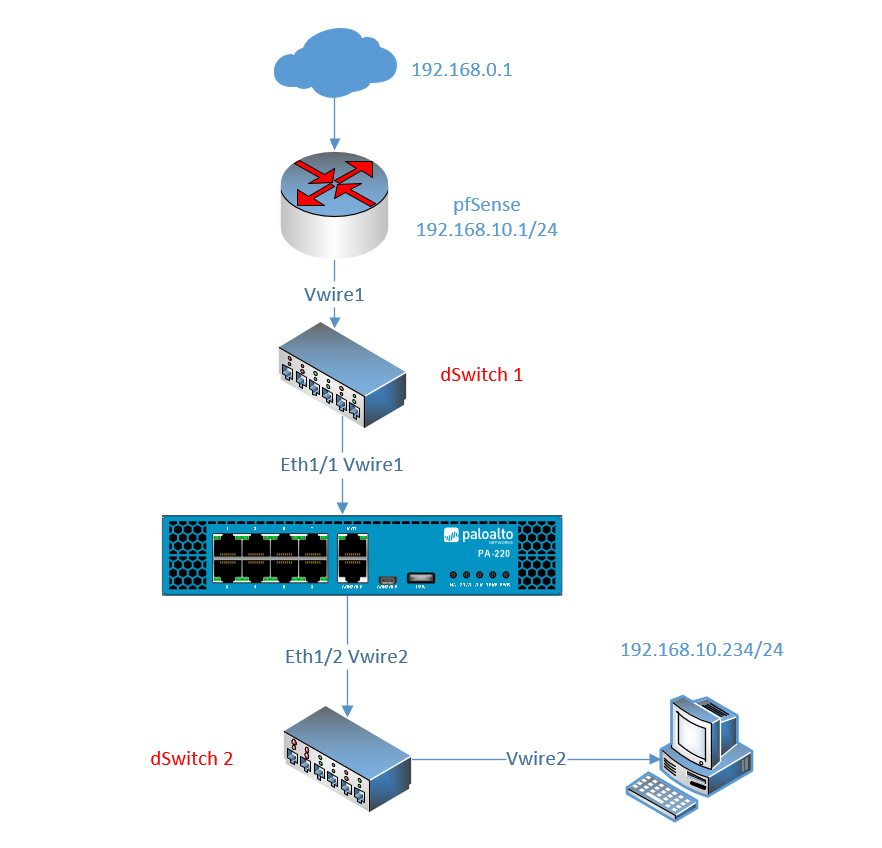
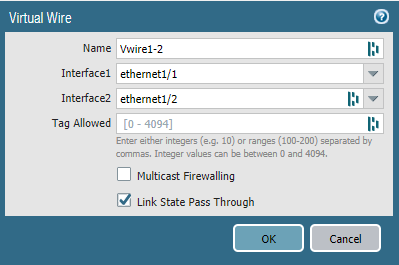
pfSense will be used as an edge router configured with a default gateway of 192.168.10.1/24 with internet access and an endpoint at 192.168.10.234/24. The NGFW will sit in-between and it’s crucial that we put the Edge Router and the NGFW behind their own switch to separate L2. There’s no need to configure IP-addresses on the NGFW and it’s not even possible with Virtual wires anyways. Vwire1 Eth1/1 interface will be used to connect the NGFW with the Edge Router pfSense. Endpoints will connect to the firewall through the Vwire2 Eth1/2 Interface.
Preparing the VM Interfaces
Create two dSwitches; “dSwitch 1” and “dSwitch 2”. Add a new portgroup called “Vwire1” to dSwitch1. And the second portgroup “Vwire2” to dSwitch2. Don’t forget to add ESXI hosts to the dSwitches.
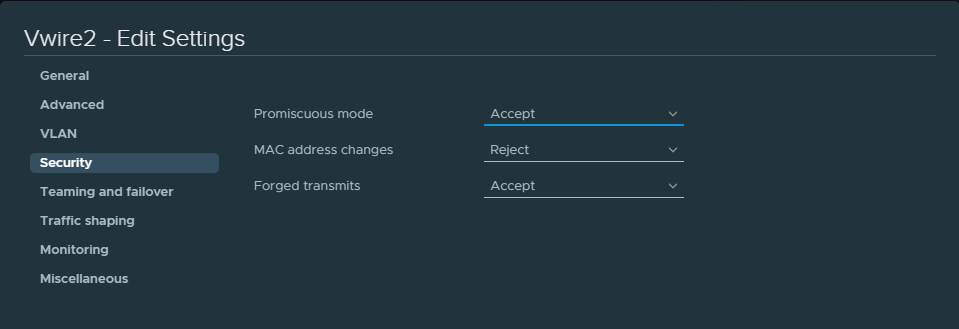
We also have to accept “Promiscuous mode” and “Forged transmits” on the portgroups Vwire 1 & Vwire 2 under the Security settings.
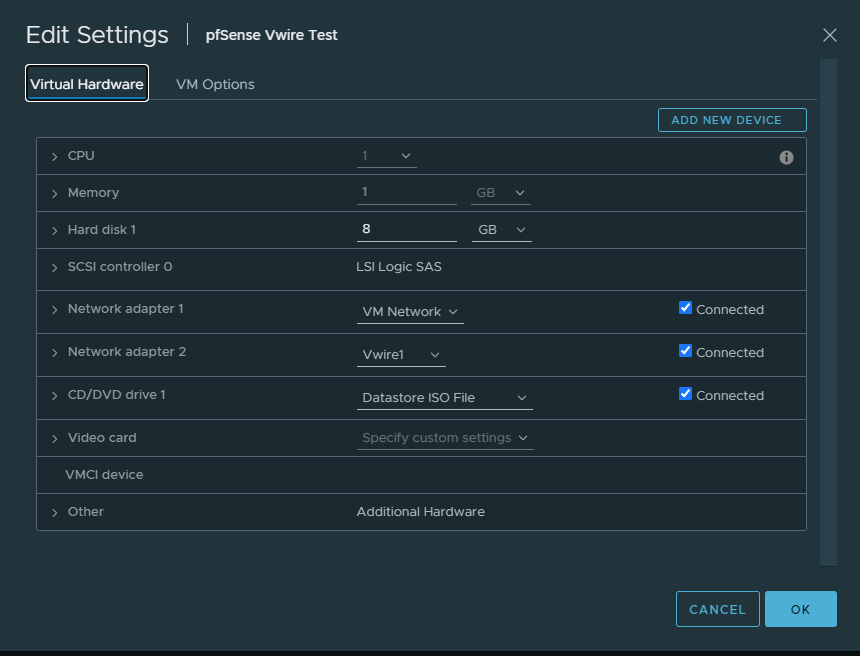
The first interface is configured as an up-link to my home network for internet access and the second interface will be used for LAN purposes.
On the Palo Alto side, the first interface will always be the management interface – which is in my case hooked up to my home network because I find it easier to access the web-interface. The second interface will be Vwire1, that’s inline with the pfSense firewall. Lastly, the 3rd interface Vwire2 will be served to the endpoints.
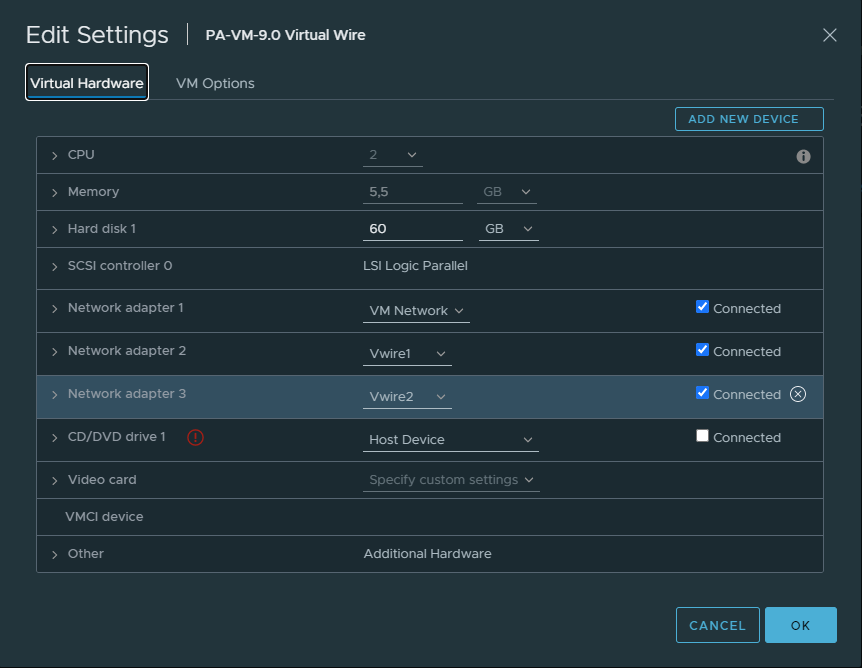
Don’t forget to change your endpoint’s portgroup to Vwire2.
Configuring the Palo Alto NGFW
Create a new Virtual Wire object: Network > Virtual Wires > Add
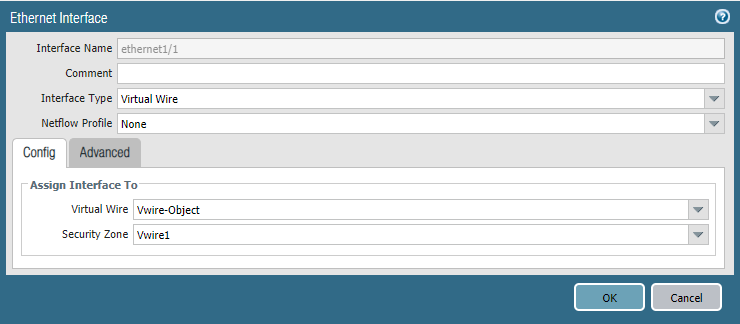
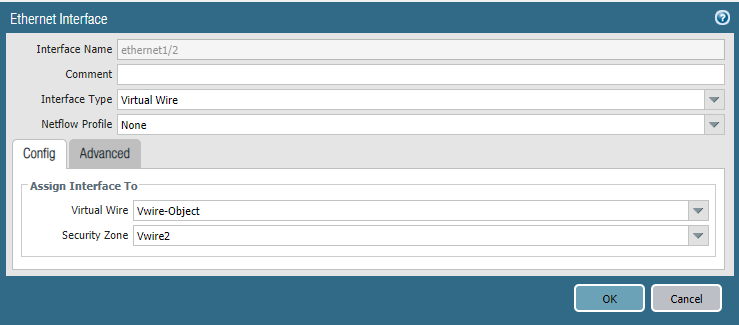
Configure Ethernet1/1 and Ethernet1/2 with the corresponding security zones: Network > Interfaces. To keep it simple I’ve named the Security Zone “Vwire1” and “Vwire2” for Eth1/1 and Eth1/2.
Finally, create some security policies to allow traffic to flow from the endpoints to the pfSense Firewall or whatever that’s used.