
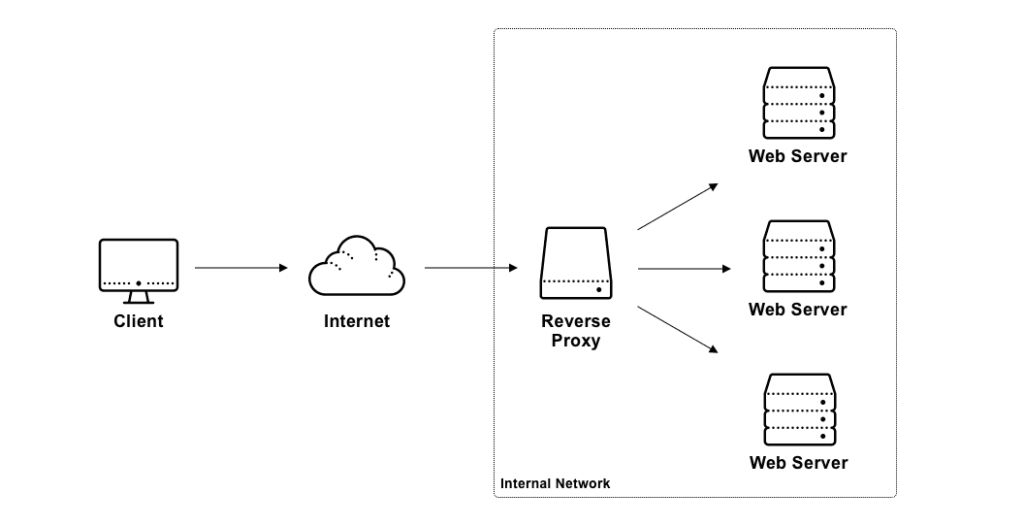
Nginx Reverse Proxy can be deployed as a Layer 7 (HTTP) or Layer 4 (TCP/UDP) Reverse Proxy. The layer 7 method is used for HTTP purposes with FQDN playing a role and Layer 4 is used for e.g. an OpenVPN server, just simply passing TCP/UDP traffic through. A reverse proxy will forward incoming requests to the appropriate back-end webserver(s). For example, a user browses to www.example.com and the Reverse Proxy redirects this request to the back-end’s private IP address.
Reverse Proxies can be detrimental when dealing with a ton of back-end servers and a limited amount of public IPv4 addresses. We can use different ports (e.g. 8443) but that requires users to add the port number to the URL. And that’s not convenient, especially if you have to remember a ton of ports. With a Reverse Proxies, we don’t have to alter the port our back-end servers listen to – because the Reverse Proxy already deals with it. So we can leave our back-end servers as is.
The other benefit to Nginx is load balancing. Sharing the load between two or more back-end servers through a set of algorithms. If there’s a given web application that is used quite a lot by your organization and battering the physical or virtual host – just add another host and implement load-balancing.
Prerequisites
- An existing and functioning webserver that’ll be used as a back-end
- Configure the Nginx Reverse Proxy as the destination for port 80 & 443
- The SSL certificates have to match on the front and back-end
Configuration example
“proxy_pass” does pretty much the magic here and the Server Block’s configuration doesn’t look too different than usual.
$ sudo vi /etc/nginx/sites-available/example.com-ssl.confserver {
listen 443 ssl;
server_name example.com www.example.com;
ssl_certificate /etc/certs/fullchain.pem; # server+Intermediate certificates
ssl_certificate_key /etc/certs/privkey.pem; # private key
include /etc/letsencrypt/options-ssl-nginx.conf;
ssl_dhparam /etc/letsencrypt/ssl-dhparams.pem;
access_log /var/log/nginx/access.log;
location / {
proxy_set_header Host $host;
proxy_set_header X-Real-IP $remote_addr;
proxy_set_header X-Forwarded-For $proxy_add_x_forwarded_for;
proxy_set_header X-Forwarded-Proto $scheme;
proxy_pass https://10.10.10.10;
#proxy_pass https://10.10.10.10:8888; # port can also be specified
}
}A global HTTP to HTTPS redirect is optional and removes the need of including it in your server blocks. You might want to remove unnecessary https redirects elsewhere since it’d be redundant.
$ sudo vi /etc/nginx/sites-available/global-http-to-https-redirect.confserver {
listen 80;
server_name _;
# this will cause it to listen to every single request
return 301 https://$host$request_uri;
# redirects it to https
}
~