
Imagine the hassle when a particular user has to login multiple times a day and remember different login/passwords and the organization resets passwords every so often. This would lead to all kinds of issues like when the user starts writing their passwords down on a piece of paper hidden under a keyboard.
SAML allows secure SSO (Single-Sign-On) authentication which means that users only have to log in once. It’s based on the XML Protocol that uses security tokens containing assertions. When the user tries to access an application or to be specific a service provider, it’ll forward the request to an Identity Provider (Okta for example) and back to the application (service provider).
In a previous post, we’ve configured RADIUS for GlobalProtect VPN which obviously lacks the SSO beauty.
Pre-requisites
- GlobalProtect Portal/Gateway configured
- LDAP integration within the Palo Alto (see my previous post)
- Okta’s AD-Agent installed and fully sync’ed with Okta
- 30 day Trial
SAML Configuration
Make sure to select the one with “SAML”. The other one is for RADIUS authentication.
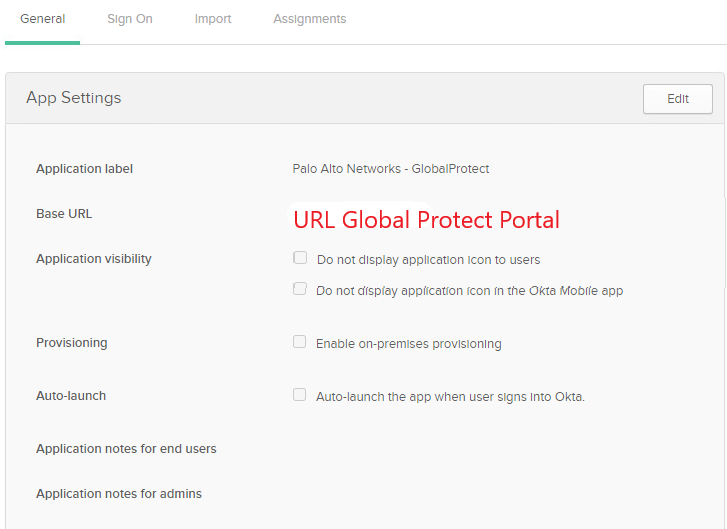
Enter the URL to your GlobalProtect as your “Base URL”. An IP address should be sufficient if you do not have a domain name.
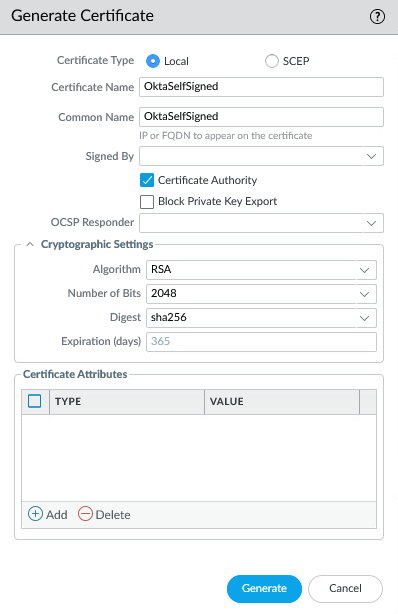
Generate some self-signed CA
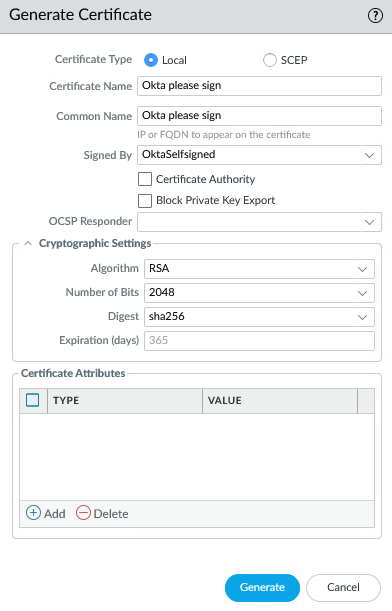
Let the self-signed CA issue a certificate.
Edit the config and enable SLO which is optional but I’d recommend doing it for the sake of following this guide.
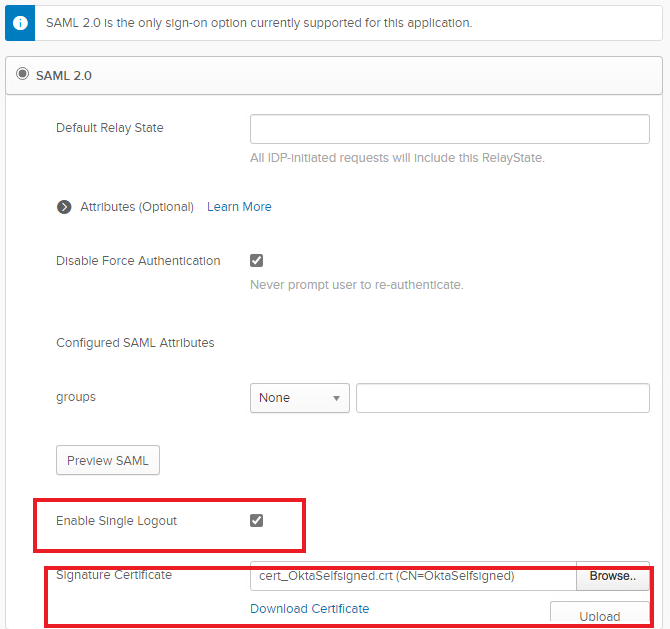
Download the metadata (right click > save as …)
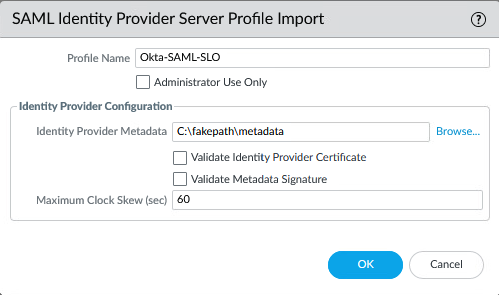
Head over to Server Profiles > SAML > Import > the metadata file you just downloaded.
Edit the SAML Server Profile and check “Sign SAML Message to IDP”
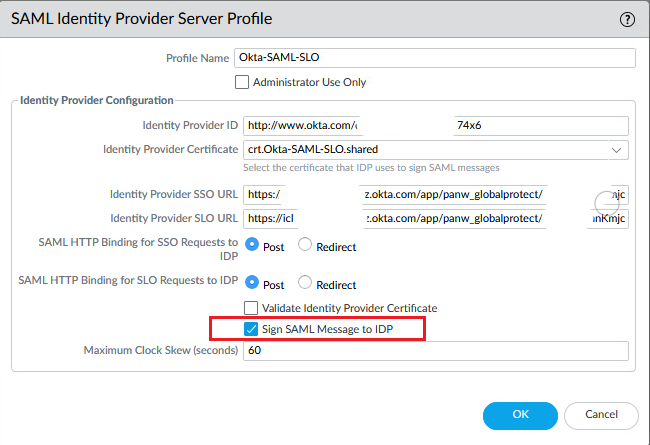
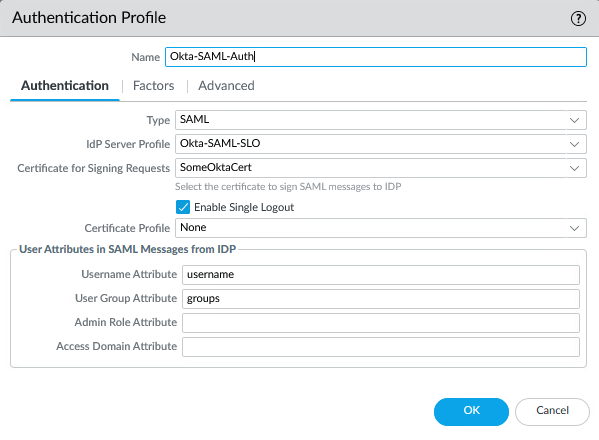
Create a new Authentication Profile (Device > Authentication Profile). Choose the Okta IdP Server Profile, the certificate that you created, enable Single Logout and fill in “groups” under “User Group Attribute”.
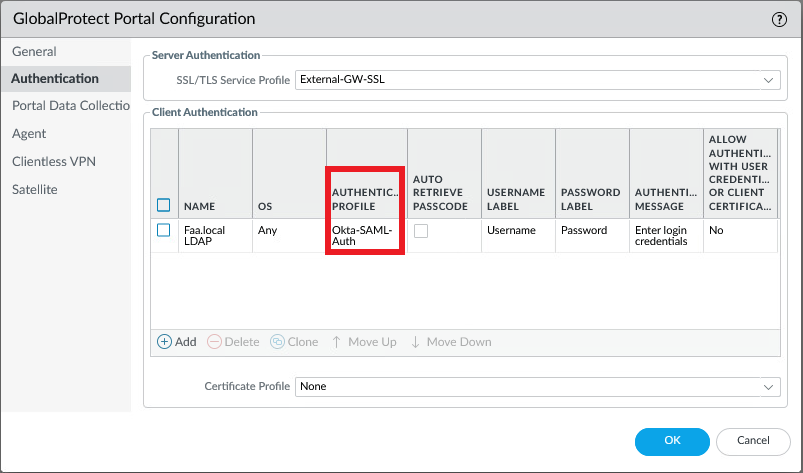
Attach the SAML Authentication Profile to the GlobalProtect Portal
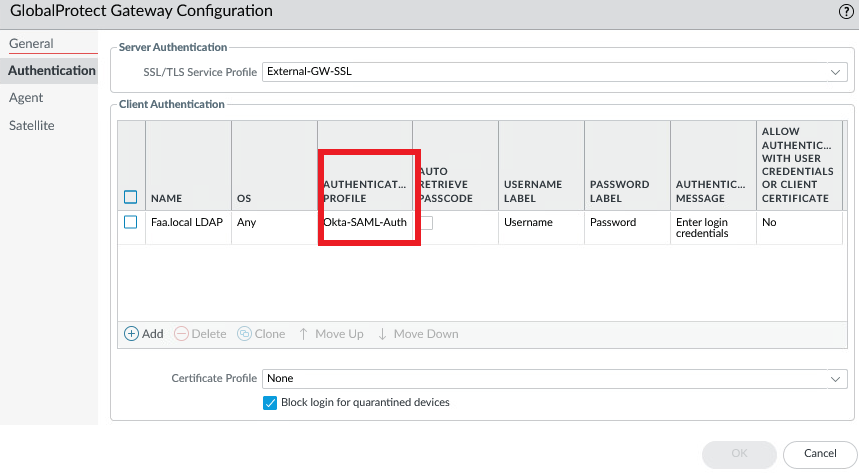
Also attach the same SAML Auth Profile to the Gateway because it’s Single-Sign-On so it doesn’t impact the user experience.
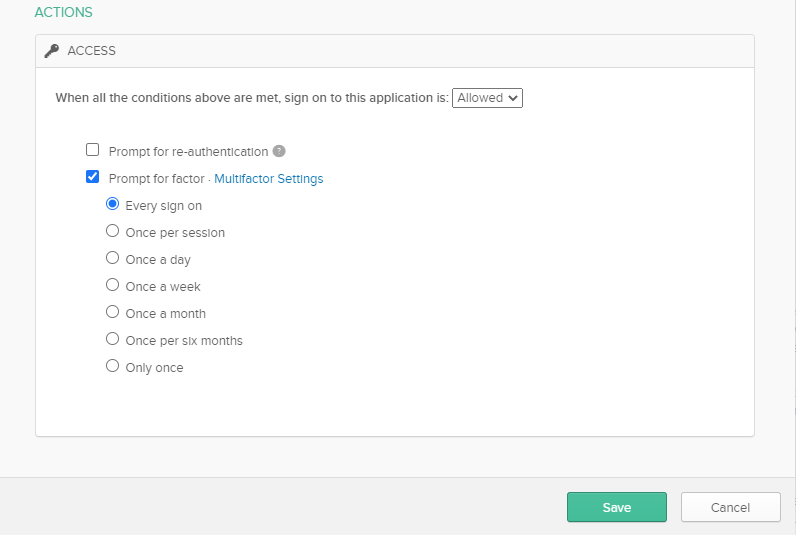
Under the GlobalProtect VPN SAML App on Okta add a new policy that users should use MFA so they have to verify their login with the App.
Conclusion
If everything is configured properly and when connecting your GlobalProtect App should prompt for your login credentials:
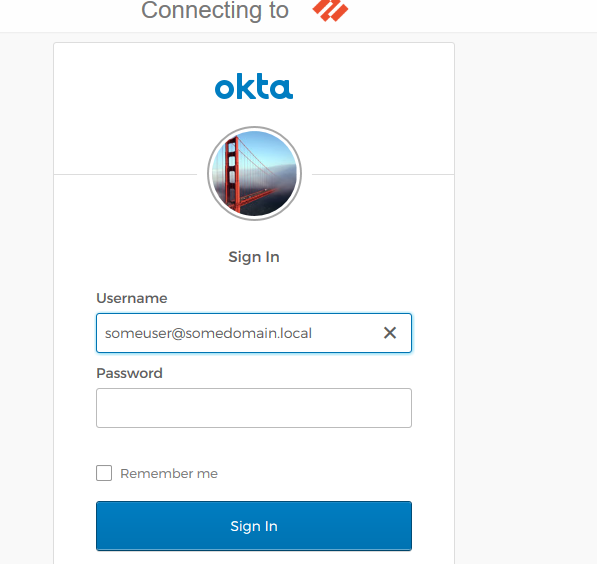
Whether you want a Push Notification or to enter a PIN-code (OTP).

Have you experience the issue that users receive 2 MFA when they sign in for the first time? If you have, do you have a workaround for this issue?
I have seen this happening in the past, but that was a long time ago. I suggest to look into authentication override, which are just cookies that you can configure for a fixed amount of time. You can configure this on the portal or on the gateway.