Imagine the hassle when a particular user has to login multiple times a day and remember different login & passwords throughout a ton of services and applications. It’s rather troublesome and annoying especially if the website/application require you to reset your password from time to time.
Users can securely authenticate with multiple applications and websites by logging in once with just one set of credentials (e.g. Active Directory). Duo supports a wide variety of SAML applications with GlobalProtect being one of them. SaaS applications such as Office 365 and many more are supported. It vastly improves the user experience, but SAML still needs to be paired with MFA for additional layers of authentication because it’s not an end-all solution that solves all security concerns.
SAML is based on the XML Protocol that uses security tokens containing assertions. When the user tries to access an application or to be specific a service provider, it’ll forward the request to an Identity Provider (Duo for example) and back to the application (service provider).
Pre-requisites
- A public domain name
- Active Directory Infrastructure matching your public domain name
- GlobalProtect Portal and Gateway configured with a public certificate
- User-ID configured on the firewall with Active Directory Integration
- Account @ duo.com with “Duo MFA” Subscription at least. A 30 day trial is available.
- A user set with Duo Mobile App
Initial configuration over at Duo Admin
First things first, install the “Palo Alto GlobalProtect – Single-Sign-On application”.
There’s another application that also supports SSO for GlobalProtect, Captive Portal and Admin UI, but that requires you to self-host the Duo Access Gateway. We’re just using the one that’s hosted by Duo which is a lot easier to set up.
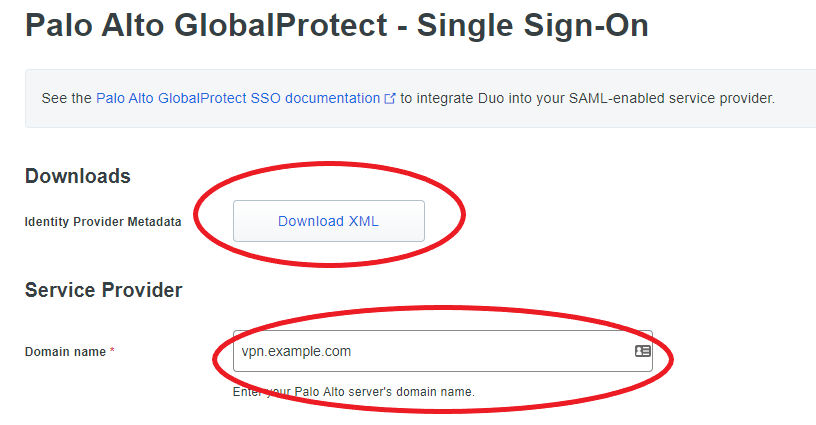
Next, configure your GlobalProtect URL and there isn’t anything else we have to change here. Export the metadata file which we will import later on the firewall.
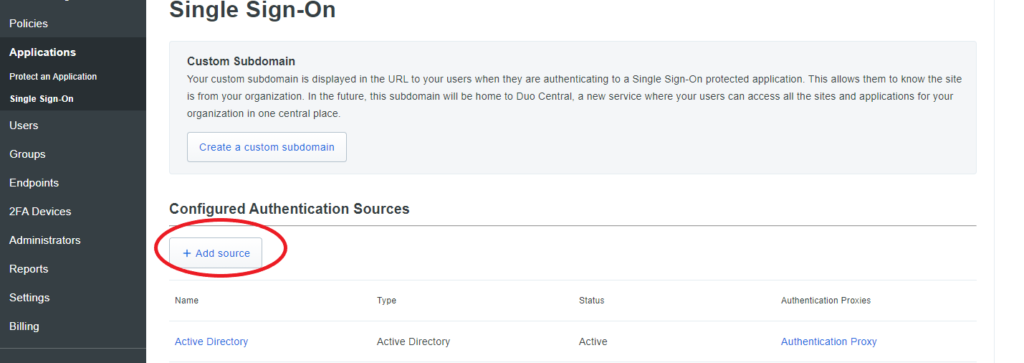
Configure source for SSO
When the GlobalProtect Portal or Gateway is configured with a SAML authentication profile, it first interacts with Duo’s application which needs a source (e.g. Active Directory) to verify the credentials users have entered.
Follow the given steps to set up the authentication proxy on any of your Domain Controllers. Make sure you do run the “Generate Command” and run the test to verify that it works.
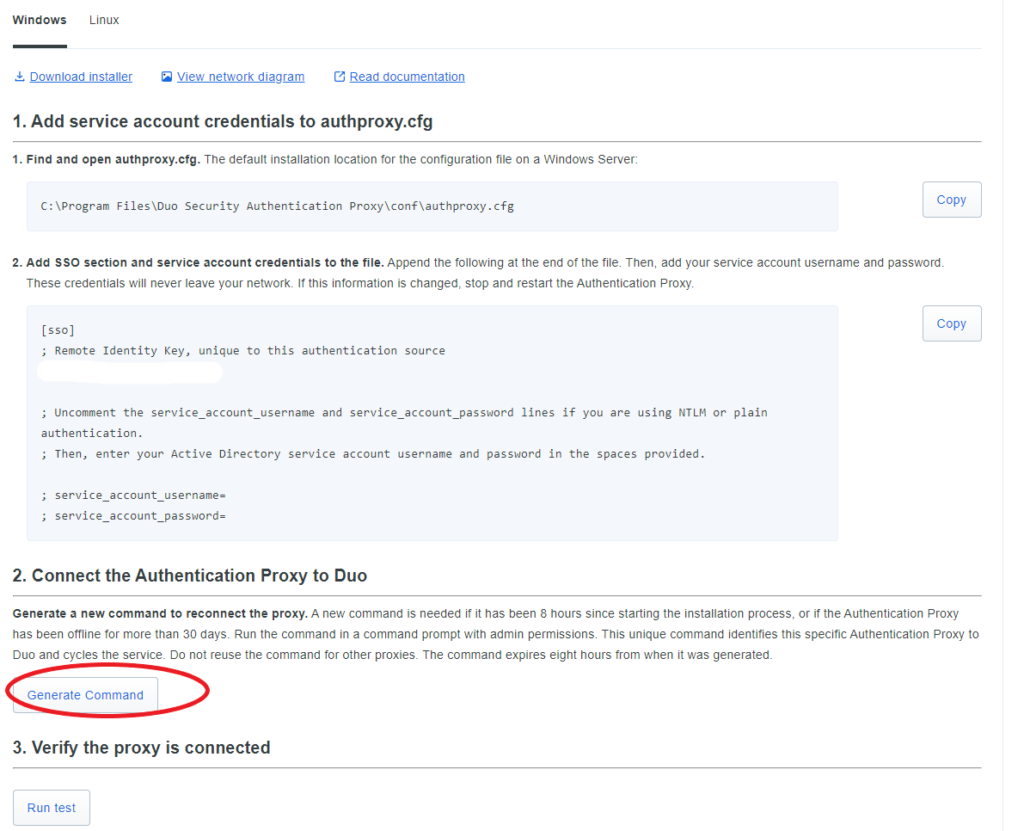
Here’s an example of how Active Directory should be configured.
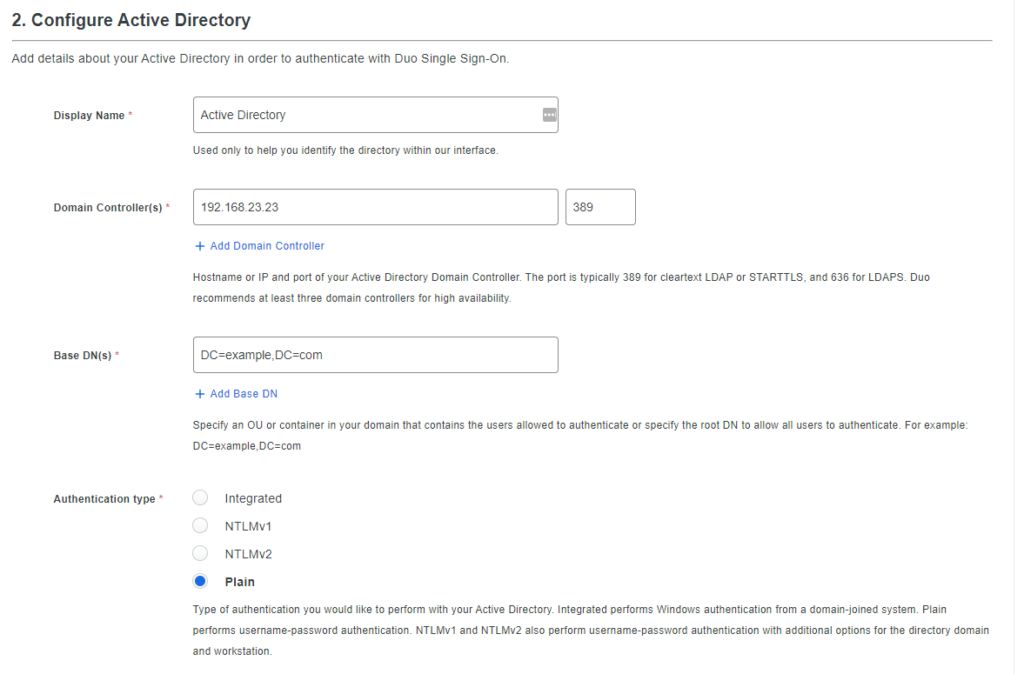
Duo requires you to enter your Email Domain although it’s not even necessary to have an email server up and running. You’ll have to verify it with a DNS challenge by adding a TXT record to your public domain name.
Make sure that the email address of your Active Directory users actually match.
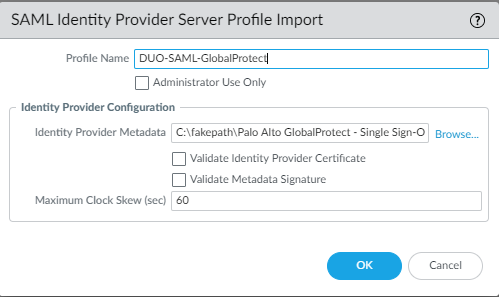
Importing SAML Metadata
Device > Server Profiles > SAML > Import
Uncheck “Validate Identity Provider Certificate”
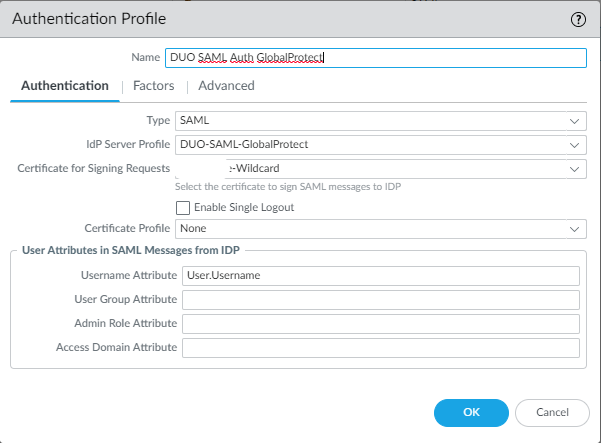
Add authentication Profile
Device > Authentication Profile > Add
Make sure to set Username Attribute to “User.Username” like below. Select the certificate you use for the GlobalProtect Portal/Gateway.
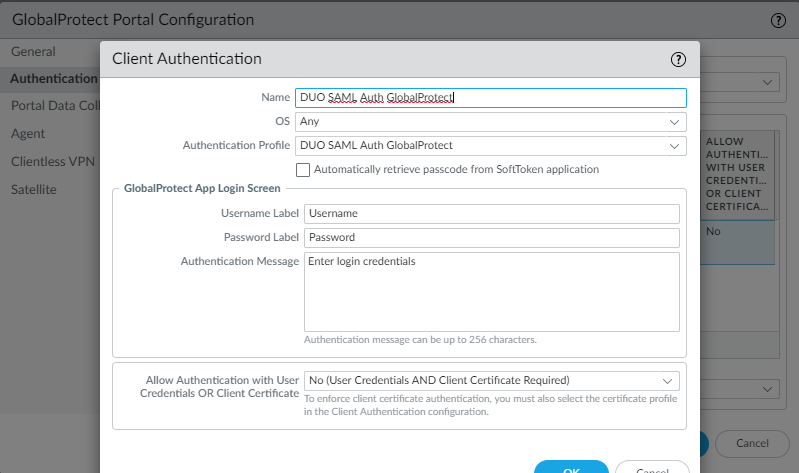
Attaching Authentication Profile to Portal/Gateway
Attach the authentication profile we just made to the GlobalProtect Portal and Gateway.
Conclusion
Once we log into the GlobalProtect Portal we’ll be prompted asking us for our credentials.
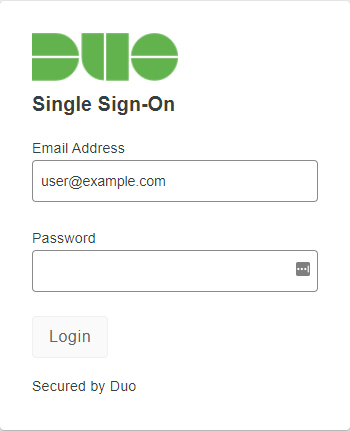
And the authentication method we prefer.