Okta started offering MFA for free when using Palo Alto Networks applications such as GlobalProtect, CaptivePortal, Admin UI and even Active Directory. Previously you were limited to just a 30-day trial. Now they offer a free subscription for those who are only interested in using the Palo Alto Networks apps.
Head over to https://www.okta.com/free/palo-alto-networks/ to get your free account! Keep in mind that you’re restricted to just Palo Alto Networks apps.
Prerequisites
- GlobalProtect configured
- Firewall configured with Active Directory authentication (User-ID)
- A free account at https://www.okta.com/free/palo-alto-networks/
Initial configuration
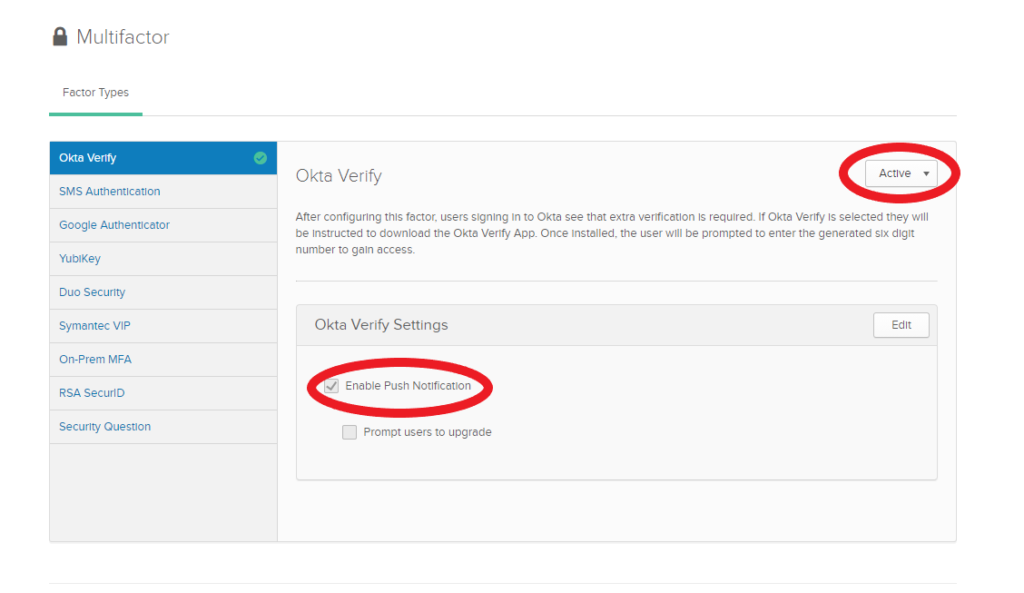
Security > Multifactor
Enable Okta Verify and Push notification as an alternative to manually typing an OTP (One-Time Password). On top of that, push notifications take advantage of PKI (Public Key Infrastructure) which is a lot more secure than OTP’s.
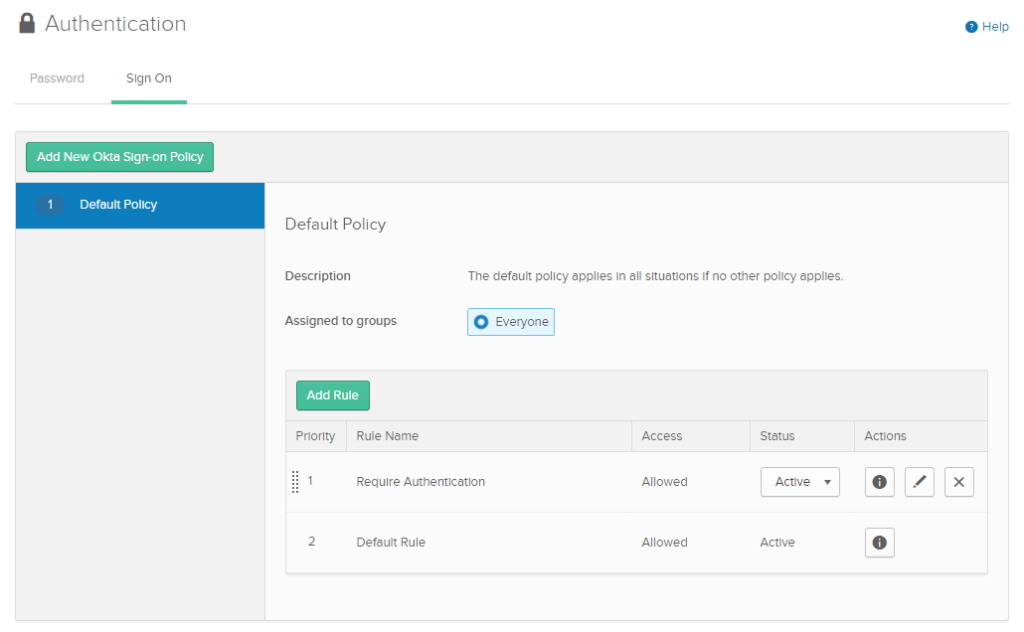
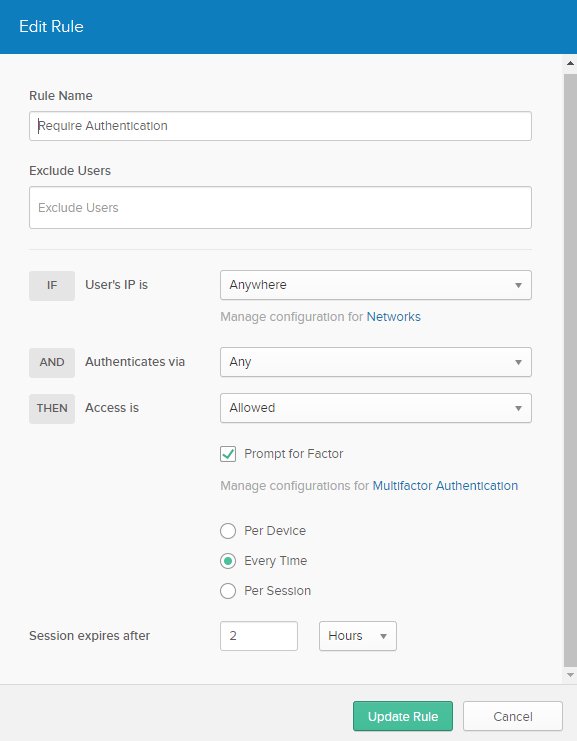
Security > Authentication > Sign On
Add a new rule so that users are prompted for factor.
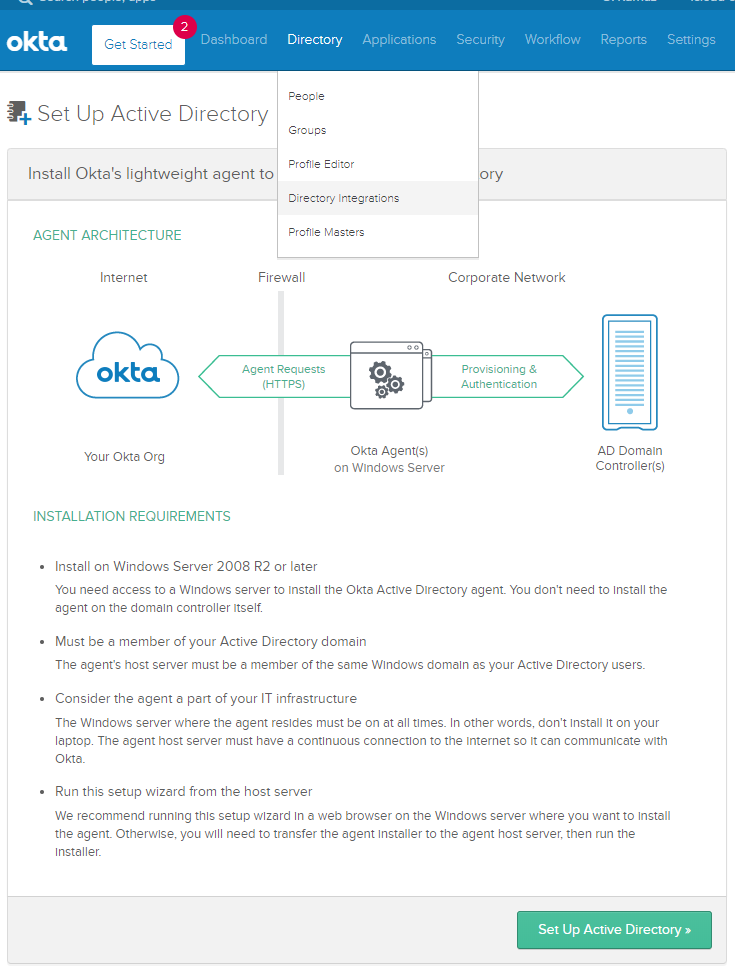
Active Directory Agent
Directory > Directory Integrations
Follow the wizard, it’s pretty straight forward. It’ll ask to install the AD-Agent and automatically create a new user named “OktaService”. Make sure that user is a member of the group “Domain Admins”. Import users and groups after it’s complete.
Make sure that Active Directory Domain users have an e-mail address. Okta will not import domain users without an e-mail address. It doesn’t have to be a valid address though.
Import it as a new user.
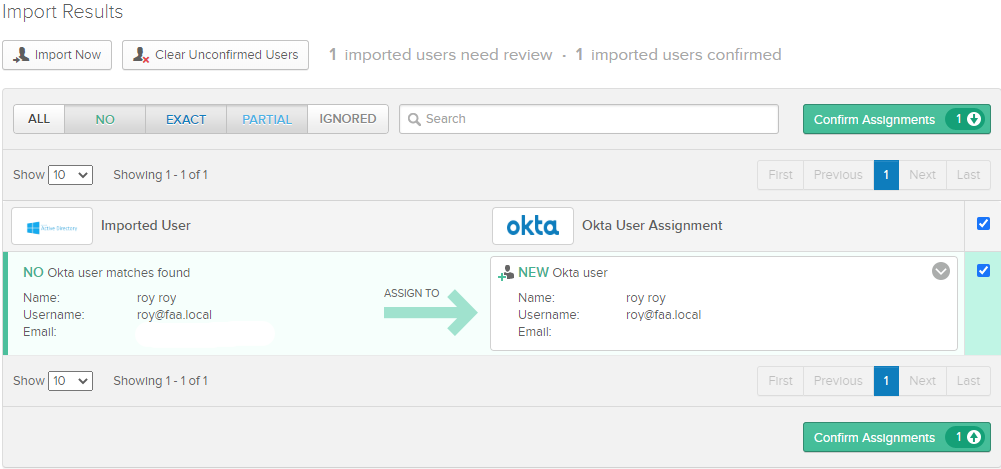
Next, head over to your organization’s URL (mycompany.okta.com) and log in with the credentials of a domain user. It’ll require you to scan a QR code with the Okta Verify app on a mobile phone.
Adding the GlobalProtect App
Applications > Applications > Add Application
Select GlobalProtect app.
Once you’ve selected the GlobalProtect App, head over to the ‘General‘ tab and enter the URL of the GlobalProtect Portal.
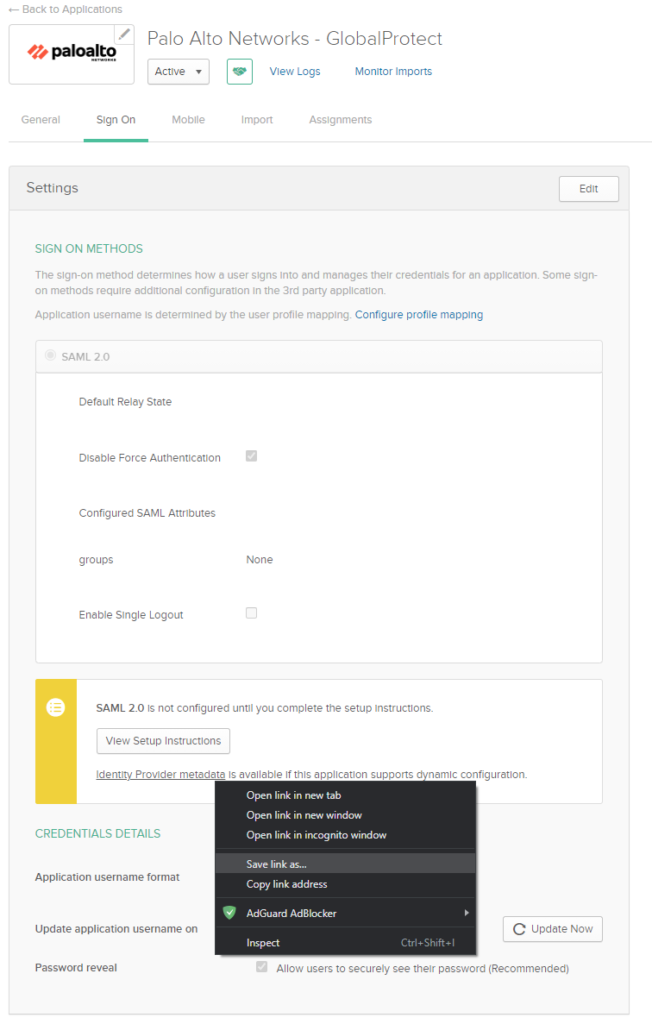
Under the ‘Sign On‘ tab, right click the IDP (Identity Provider) metadata file which we will import on the firewall later on.
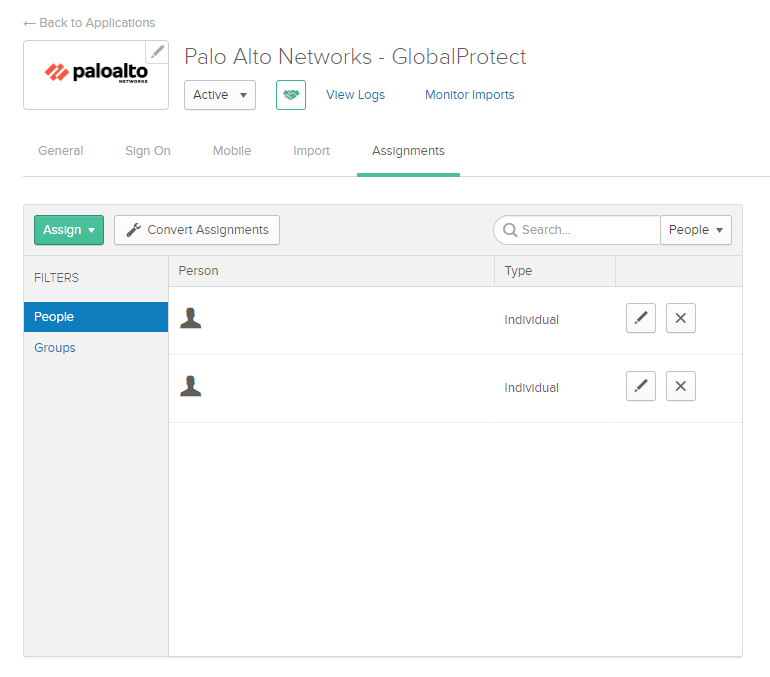
Under the ‘Assignments’ tab, add your domain users who use GlobalProtect. I removed the names due to privacy reasons.
Server & Authentication Profile on firewall
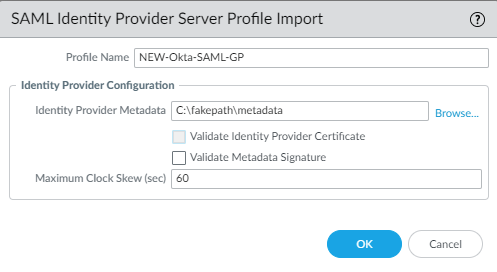
Device > Server Profiles > SAML > Import
Select the metadata file and uncheck the box “Validate Identity Provider Certificate”.
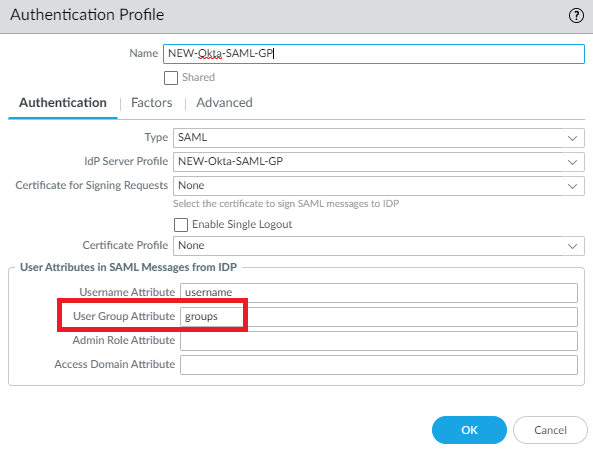
Device > Authentication Profile > Add
Select the SAML Server Profile. Add the attribute ‘groups’ to User Group Attribute field.
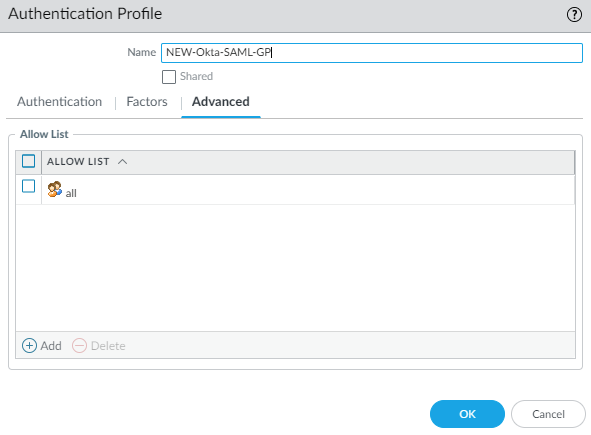
And allow all under advanced. There’s no reason to specify users here even from a security standpoint because it’s just an authentication profile. You can restrict user access at the Portal/Gateway or at Okta.
Lastly, update the GlobalProtect Portal & Gateway with the new authentication profile.
Network > GlobalProtect > Portal/Gateway > Authentication
2 responses to “Free Okta MFA for Palo Alto Networks GlobalProtect”
hi can we use this as local user instead?
Hey, thank you for your question!
And yes, you can use this with a local user. So you would: Create a new user in the directory of Okta and assign the user to the GlobalProtect App.
2) Extract the metadata file from the links given in the App and use this in a SAML server profile.
3) Create an authentication profile referencing to the SAML server profile.
4) Use the authentication profile attached to your gateway and portal.