
In case there are sources attempting malicious attempts at your environment, we can blacklist them automatically if they exceed a certain severity threshold and tag them, so they are automatically denied by a security policy rather than going through another security phase over and over. Basically quarantining them.
Create a tag
Go to Objects > Tag
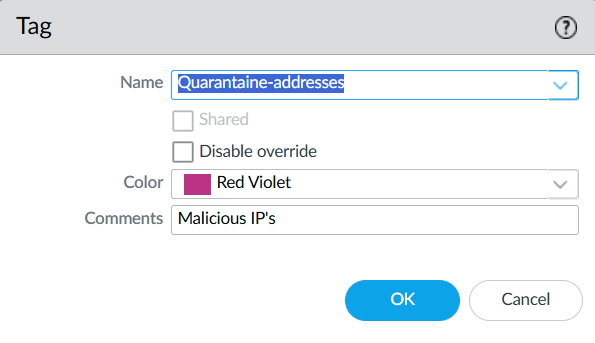
As you can see I’ve named it “Quarantaine-addresses”. Choose a color of your choice and add a comment.
Creating a log forwarding profile
Go to Objects Log Forwarding
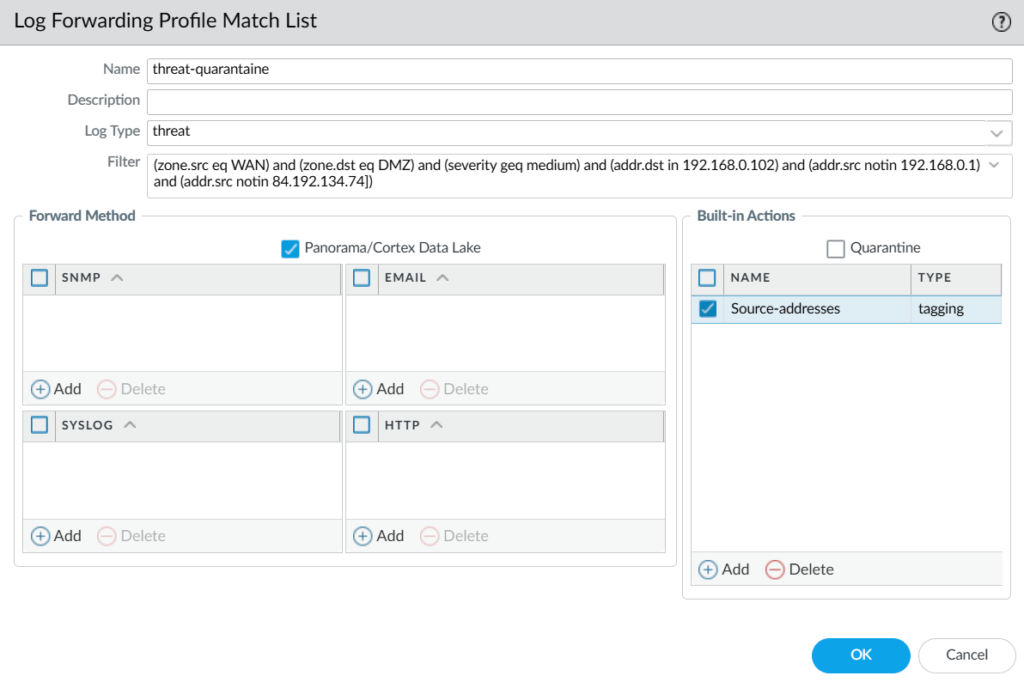
I’ve configured the src zone to be my “WAN” security zone and the destination zone “DMZ”, with a severity of greater of equal than medium. And a couple of exception are made. Select the log type as threat.
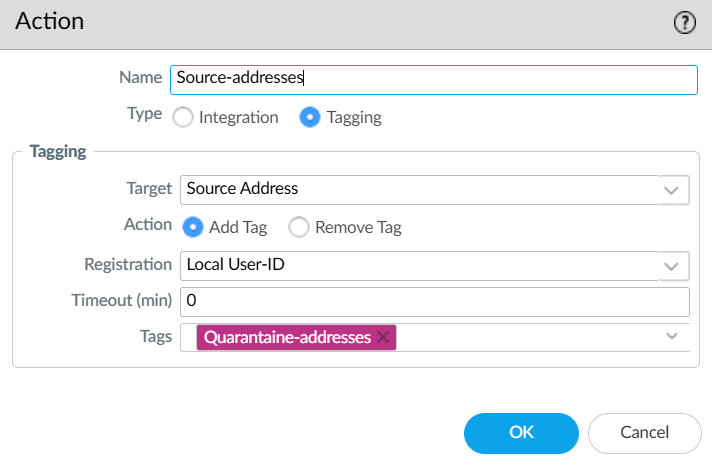
After this, you’ll have to configure Built-in Actions, see the following screenshot how I’ve configured it. Make sure to select the tag that you created earlier.
Address groups
We’ll need to maintain a list of addresses in a group to blacklist, here’s how we configure it.
Go to Objects > Addresses groups
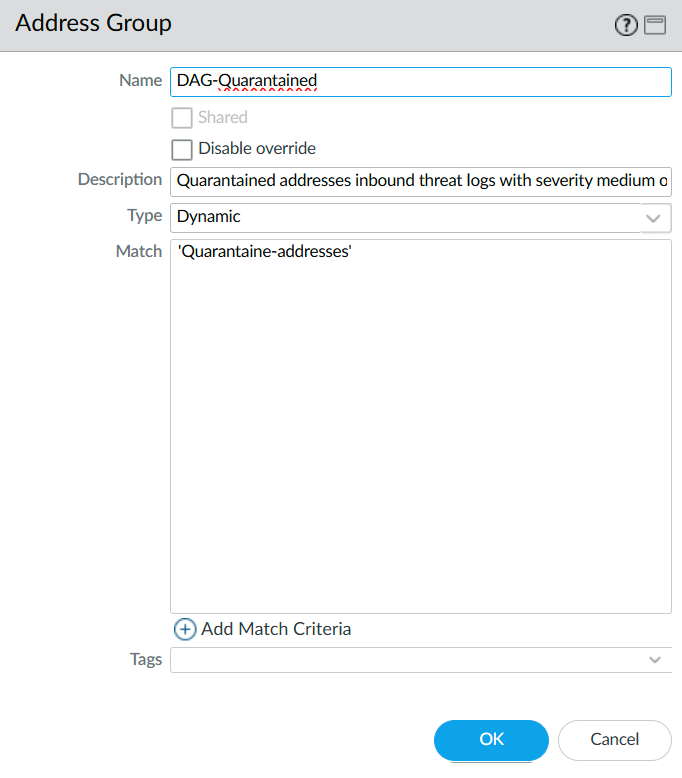
Select the “Quarantaine-addresses” tag address we created.
Adding a security policy to block the quarantaine addresses.
I already have a block security profile in-place for my webserver, so all I’ve had to do it is add the address group.
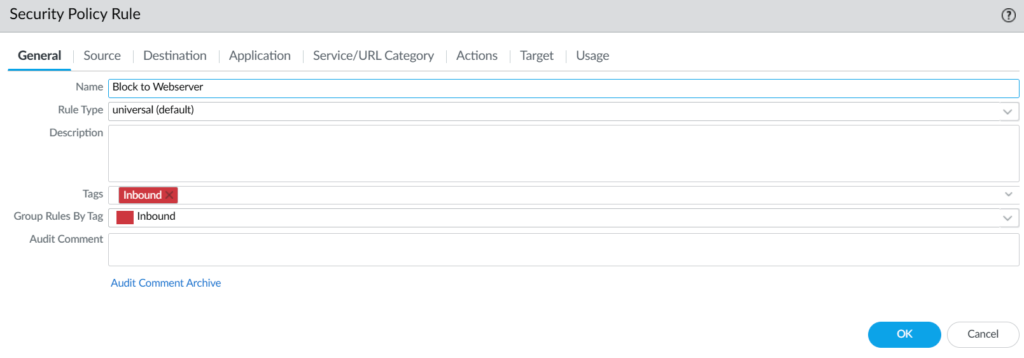
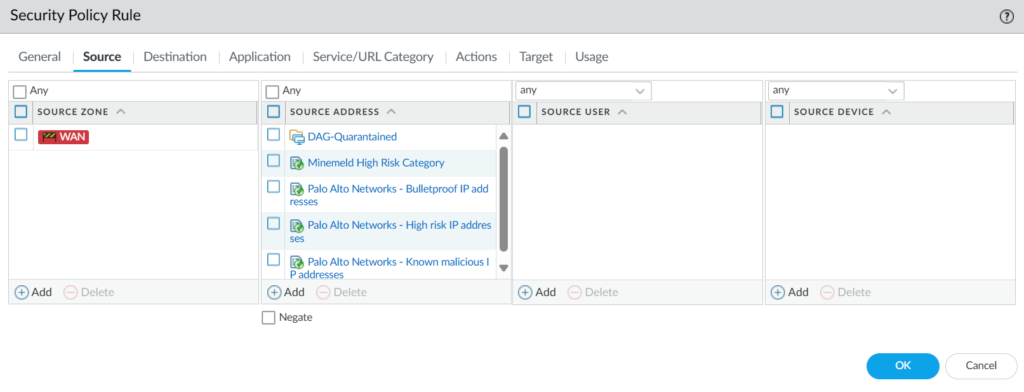
Here we can see “DAG-quarantaine” address group included in the source address field.
Checking which IP addresses are blocked
This has to be done on the firewall itself, Panorama will not show it.
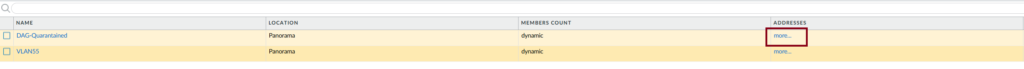
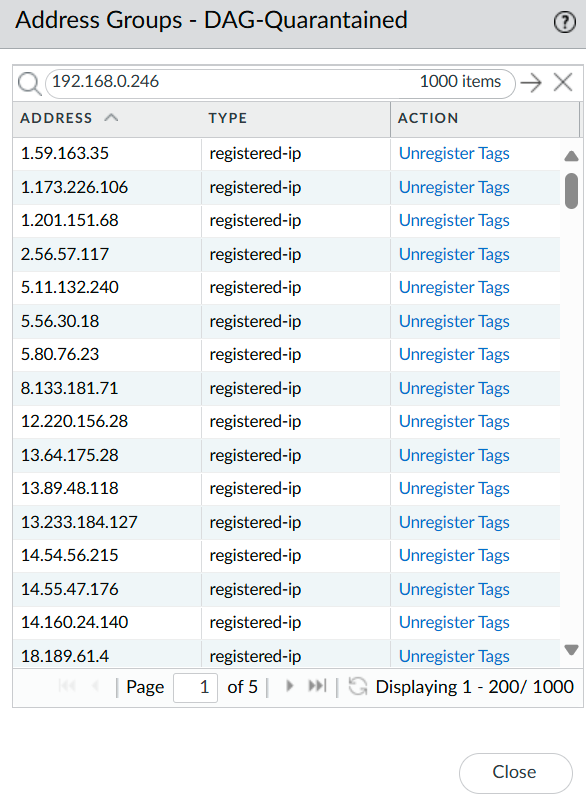
Here we can see the list of IP addresses that are blocked and we can unregister them by clicking on “Unregister tags” in case of a false positive. There’s also a search bar to easily find the IP address that you’re looking for.